Jan 31, 2024NewsroomVulnerability / Zero Day Ivanti is alerting of two new high-severity flaws in its Connect Secure and Policy Secure products, one of which is said to have come under targeted exploitation in the wild. The list of vulnerabilities is as follows - CVE-2024-21888 (CVSS score: 8.8) - A privilege escalation vulnerability in the web component of Ivanti Connect … [Read more...] about Ivanti Discloses 2 New Zero-Day Flaws, One Under Active Exploitation
active
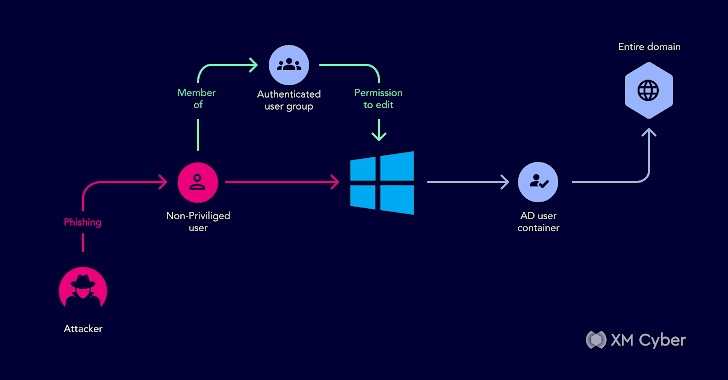
Understanding Active Directory Attack Paths to Improve Security
Introduced in 1999, Microsoft Active Directory is the default identity and access management service in Windows networks, responsible for assigning and enforcing security policies for all network endpoints. With it, users can access various resources across networks. As things tend to do, times, they are a'changin' – and a few years back, Microsoft introduced Azure Active … [Read more...] about Understanding Active Directory Attack Paths to Improve Security
Severe Android and Novi Survey Vulnerabilities Under Active Exploitation
Apr 14, 2023Ravie LakshmananMobile Security / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The two flaws are listed below - CVE-2023-20963 (CVSS score: 7.8) - Android Framework Privilege Escalation … [Read more...] about Severe Android and Novi Survey Vulnerabilities Under Active Exploitation
Microsoft Issues Patches for 97 Flaws, Including Active Ransomware Exploit
Apr 12, 2023Ravie LakshmananPatch Tuesday / Software Updates It's the second Tuesday of the month, and Microsoft has released another set of security updates to fix a total of 97 flaws impacting its software, one of which has been actively exploited in ransomware attacks in the wild. Seven of the 97 bugs are rated Critical and 90 are rated Important in severity. … [Read more...] about Microsoft Issues Patches for 97 Flaws, Including Active Ransomware Exploit
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation
Apr 01, 2023Ravie LakshmananCyber Attack / Vulnerability Critical security flaws in Cacti, Realtek, and IBM Aspera Faspex are being exploited by various threat actors in hacks targeting unpatched systems. This entails the abuse of CVE-2022-46169 (CVSS score: 9.8) and CVE-2021-35394 (CVSS score: 9.8) to deliver MooBot and ShellBot (aka PerlBot), Fortinet FortiGuard Labs said … [Read more...] about Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation
CISA Issues Warning on Active Exploitation of ZK Java Web Framework Vulnerability
Feb 28, 2023Ravie LakshmananSoftware Security / Cyber Attack The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity flaw affecting the ZK Framework to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation. Tracked as CVE-2022-36537 (CVSS score: 7.5), the issue impacts ZK Framework versions 9.6.1, … [Read more...] about CISA Issues Warning on Active Exploitation of ZK Java Web Framework Vulnerability
CISA Warns of Active Attacks Exploiting Fortra MFT, TerraMaster NAS, and Intel Driver Flaws
Feb 11, 2023Ravie LakshmananThreat Response / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added three flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active abuse in the wild. Included among the three is CVE-2022-24990, a bug affecting TerraMaster network-attached storage (TNAS) devices that could … [Read more...] about CISA Warns of Active Attacks Exploiting Fortra MFT, TerraMaster NAS, and Intel Driver Flaws
Active Directory Domain Compromised in Under 24 Hours
Jan 12, 2023Ravie LakshmananActive Directory / Malware A recent IcedID malware attack enabled the threat actor to compromise the Active Directory domain of an unnamed target less than 24 hours after gaining initial access, while also borrowing techniques from other groups like Conti to meet its goals. "Throughout the attack, the attacker followed a routine of recon commands, … [Read more...] about Active Directory Domain Compromised in Under 24 Hours
CISA Warns of Active exploitation of JasperReports Vulnerabilities
Dec 30, 2022Ravie LakshmananPatch Management The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two-years-old security flaws impacting TIBCO Software's JasperReports product to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The flaws, tracked as CVE-2018-5430 (CVSS score: 7.7) and CVE-2018-18809 (CVSS score: … [Read more...] about CISA Warns of Active exploitation of JasperReports Vulnerabilities
Active Directory Bugs Could Let hackers Take Over Windows Domain Controllers
Microsoft is urging customers to patch two security vulnerabilities in Active Directory domain controllers that it addressed in November following the availability of a proof-of-concept (PoC) tool on December 12. The two vulnerabilities — tracked as CVE-2021-42278 and CVE-2021-42287 — have a severity rating of 7.5 out of a maximum of 10 and concern a privilege escalation flaw … [Read more...] about Active Directory Bugs Could Let hackers Take Over Windows Domain Controllers