As we continue to iterate and help organizations meet their observability goals, Logz.io is thrilled to announce we’ve earned over a dozen Winter 2023 G2 Badges for our Logz.io Open 360™ essential observability platform!G2 Research is a tech marketplace where people can discover, review, and manage the software they need to reach their potential. Here are the Winter 2023 G2 … [Read more...] about Logz.io’s Open 360 Observability Platform Takes Home Over a Dozen Winter G2 Badges
dozen
Microsoft Bug Allowed Hackers to Breach Over Two Dozen Organizations via Forged Azure AD Tokens
Jul 15, 2023THNCyber Attack / Enterprise Security Microsoft on Friday said a validation error in its source code allowed for Azure Active Directory (Azure AD) tokens to be forged by a malicious actor known as Storm-0558 using a Microsoft account (MSA) consumer signing key to breach two dozen organizations. "Storm-0558 acquired an inactive MSA consumer signing key and used it … [Read more...] about Microsoft Bug Allowed Hackers to Breach Over Two Dozen Organizations via Forged Azure AD Tokens
Over a Dozen PHP Packages with 500 Million Compromised
May 05, 2023Ravie LakshmananProgramming / Software Security PHP software package repository Packagist revealed that an "attacker" gained access to four inactive accounts on the platform to hijack over a dozen packages with over 500 million installs to date. "The attacker forked each of the packages and replaced the package description in composer.json with their own message … [Read more...] about Over a Dozen PHP Packages with 500 Million Compromised
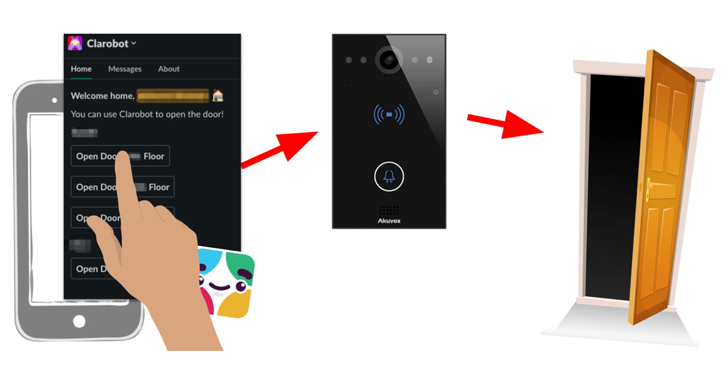
Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom
Mar 13, 2023Ravie LakshmananEnterprise Security / Privacy More than a dozen security flaws have been disclosed in E11, a smart intercom product made by Chinese company Akuvox. "The vulnerabilities could allow attackers to execute code remotely in order to activate and control the device's camera and microphone, steal video and images, or gain a network foothold," Claroty … [Read more...] about Researchers Uncover Over a Dozen Security Flaws in Akuvox E11 Smart Intercom
New Linux Malware Exploiting Over Two Dozen CMS Flaws
Jan 02, 2023Ravie LakshmananWeb Security / Linux WordPress sites are being targeted by a previously unknown strain of Linux malware that exploits flaws in over two dozen plugins and themes to compromise vulnerable systems. "If sites use outdated versions of such add-ons, lacking crucial fixes, the targeted web pages are injected with malicious JavaScripts," Russian security … [Read more...] about New Linux Malware Exploiting Over Two Dozen CMS Flaws
New Go-based Zerobot Botnet Exploiting Dozen of IoT Vulnerabilities to Expand its Network
Dec 07, 2022Ravie LakshmananInternet of Things / Botnet A novel Go-based botnet called Zerobot has been observed in the wild proliferating by taking advantage of nearly two dozen security vulnerabilities in the internet of things (IoT) devices and other software. The botnet "contains several modules, including self-replication, attacks for different protocols, and … [Read more...] about New Go-based Zerobot Botnet Exploiting Dozen of IoT Vulnerabilities to Expand its Network
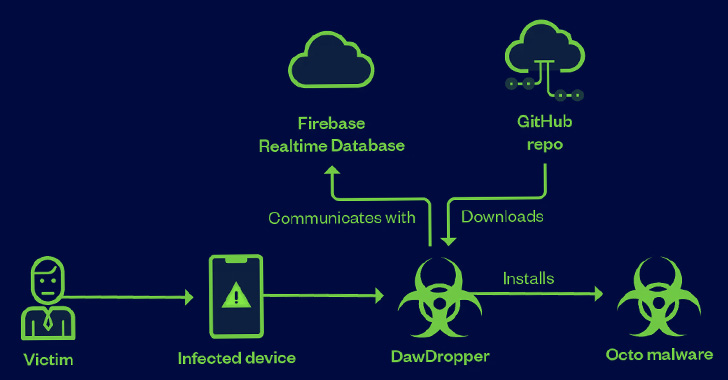
Over a Dozen Android Apps on Google Play Store Caught Dropping Banking Malware
A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Play Store to compromise users' devices with banking malware. These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such as document scanners, QR code readers, VPN services, and call recorders, among others. All these apps in … [Read more...] about Over a Dozen Android Apps on Google Play Store Caught Dropping Banking Malware
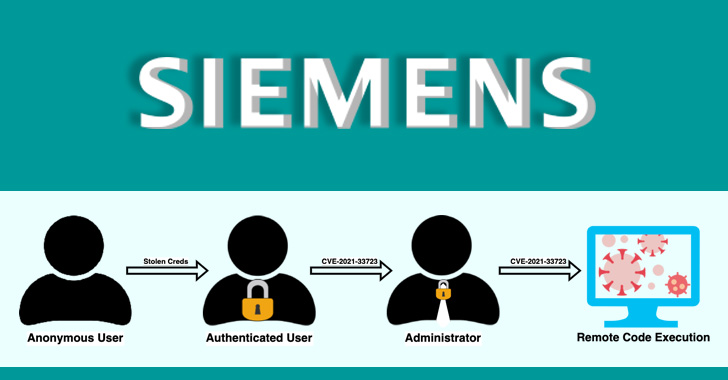
Over a Dozen Flaws Found in Siemens’ Industrial Network Management System
Cybersecurity researchers have disclosed details about 15 security flaws in Siemens SINEC network management system (NMS), some of which could be chained by an attacker to achieve remote code execution on affected systems. "The vulnerabilities, if exploited, pose a number of risks to Siemens devices on the network including denial-of-service attacks, credential leaks, and … [Read more...] about Over a Dozen Flaws Found in Siemens’ Industrial Network Management System
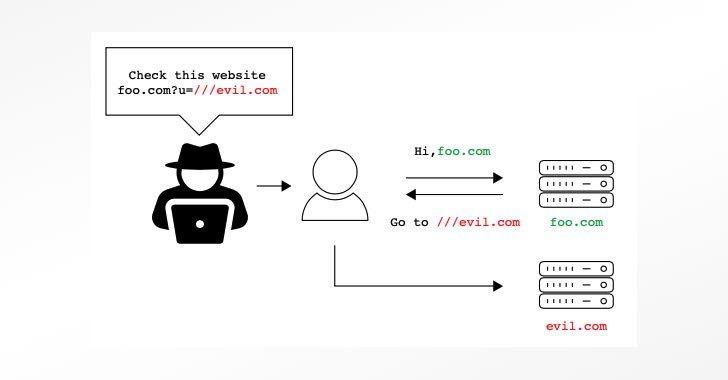
Researchers Find Bugs in Over A Dozen Widely Used URL Parser Libraries
A study of 16 different Uniform Resource Locator (URL) parsing libraries has unearthed inconsistencies and confusions that could be exploited to bypass validations and open the door to a wide range of attack vectors. In a deep-dive analysis jointly conducted by cybersecurity firms Claroty and Synk, eight security vulnerabilities were identified in as many third-party libraries … [Read more...] about Researchers Find Bugs in Over A Dozen Widely Used URL Parser Libraries