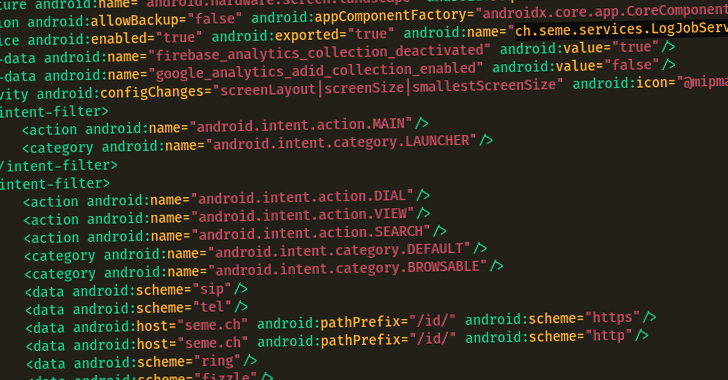
The relationship between various TDSs and DNS associated with Vigorish Viper and the final landing experience for the user A Chinese organized crime syndicate with links to money laundering and human trafficking across Southeast Asia has been using an advanced "technology suite" that runs the whole cybercrime supply chain spectrum to spearhead its operations. Infoblox is … [Read more...] about Experts Uncover Chinese Cybercrime Network Behind Gambling and Human Trafficking
Experts
Experts Find Flaw in Replicate AI Service Exposing Customers’ Models and Data
May 25, 2024NewsroomMachine Learning / Data Breach Cybersecurity researchers have discovered a critical security flaw in an artificial intelligence (AI)-as-a-service provider Replicate that could have allowed threat actors to gain access to proprietary AI models and sensitive information. "Exploitation of this vulnerability would have allowed unauthorized access to the AI … [Read more...] about Experts Find Flaw in Replicate AI Service Exposing Customers’ Models and Data
Experts Warn of macOS Backdoor Hidden in Pirated Versions of Popular Software
Jan 19, 2024NewsroomMalware / Endpoint Security Pirated applications targeting Apple macOS users have been observed containing a backdoor capable of granting attackers remote control to infected machines. "These applications are being hosted on Chinese pirating websites in order to gain victims," Jamf Threat Labs researchers Ferdous Saljooki and Jaron Bradley said. "Once … [Read more...] about Experts Warn of macOS Backdoor Hidden in Pirated Versions of Popular Software
Experts Uncover Passive Method to Extract Private RSA Keys from SSH Connections
Nov 27, 2023NewsroomServer Security / Encryption A new study has demonstrated that it's possible for passive network attackers to obtain private RSA host keys from a vulnerable SSH server by observing when naturally occurring computational faults that occur while the connection is being established. The Secure Shell (SSH) protocol is a method for securely transmitting … [Read more...] about Experts Uncover Passive Method to Extract Private RSA Keys from SSH Connections
Experts Discover Flaw in U.S. Govt’s Chosen Quantum-Resistant Encryption Algorithm
Mar 06, 2023Ravie LakshmananEncryption / Cybersecurity A group of researchers has revealed what it says is a vulnerability in a specific implementation of CRYSTALS-Kyber, one of the encryption algorithms chosen by the U.S. government as quantum-resistant last year. The exploit relates to "side-channel attacks on up to the fifth-order masked implementations of CRYSTALS-Kyber … [Read more...] about Experts Discover Flaw in U.S. Govt’s Chosen Quantum-Resistant Encryption Algorithm
Experts Warn of RambleOn Android Malware Targeting South Korean Journalists
Feb 17, 2023Ravie LakshmananMobile Security / Cyber Threat Suspected North Korean nation-state actors targeted a journalist in South Korea with a malware-laced Android app as part of a social engineering campaign. The findings come from South Korea-based non-profit Interlab, which coined the new malware RambleOn. The malicious functionalities include the "ability to read and … [Read more...] about Experts Warn of RambleOn Android Malware Targeting South Korean Journalists
Experts Uncover Two Long-Running Android Spyware Campaigns Targeting Uyghurs
Two long-running surveillance campaigns have been found targeting the Uyghur community in China and elsewhere with Android spyware tools designed to harvest sensitive information and track their whereabouts. This encompasses a previously undocumented malware strain called BadBazaar and updated variants of an espionage artifact dubbed MOONSHINE by researchers from the University … [Read more...] about Experts Uncover Two Long-Running Android Spyware Campaigns Targeting Uyghurs
Experts Warn of New RatMilad Android Spyware Targeting Enterprise Devices
A novel Android malware called RatMilad has been observed targeting a Middle Eastern enterprise mobile device by concealing itself as a VPN and phone number spoofing app. The mobile trojan functions as advanced spyware with capabilities that receives and executes commands to collect and exfiltrate a wide variety of data from the infected mobile endpoint, Zimperium said in a … [Read more...] about Experts Warn of New RatMilad Android Spyware Targeting Enterprise Devices
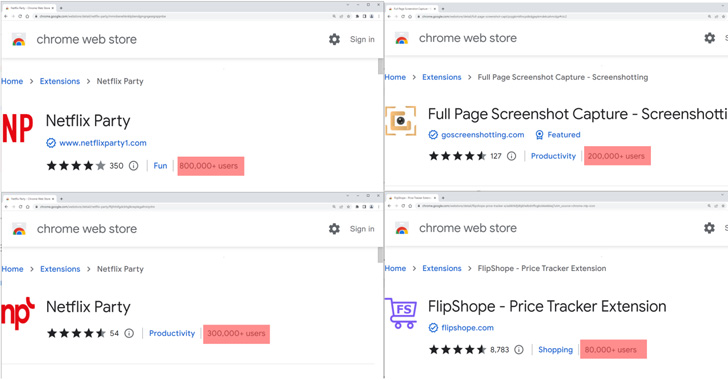
Experts Find Malicious Cookie Stuffing Chrome Extensions Used by 1.4 Million Users
Five imposter extensions for the Google Chrome web browser masquerading as Netflix viewers and others have been found to track users' browsing activity and profit of retail affiliate programs. "The extensions offer various functions such as enabling users to watch Netflix shows together, website coupons, and taking screenshots of a website," McAfee researchers Oliver Devane and … [Read more...] about Experts Find Malicious Cookie Stuffing Chrome Extensions Used by 1.4 Million Users
Experts Find Similarities Between New LockBit 3.0 and BlackMatter Ransomware
Cybersecurity researchers have reiterated similarities between the latest iteration of the LockBit ransomware and BlackMatter, a rebranded variant of the DarkSide ransomware strain that closed shop in November 2021. The new version of LockBit, called LockBit 3.0 aka LockBit Black, was released in June 2022, launching a brand new leak site and what's the very first ransomware … [Read more...] about Experts Find Similarities Between New LockBit 3.0 and BlackMatter Ransomware