While log parsing isn’t very sexy and never gets much credit, it is fundamental to productive and centralized log analysis. Log parsing extracts information in your logs and organizes them into fields. Without well-structured fields in your logs, searching and visualizing your log data is near impossible.In this article, we’ll review some of the more popular technologies for … [Read more...] about A Guide to Log File Parsing Tools
File
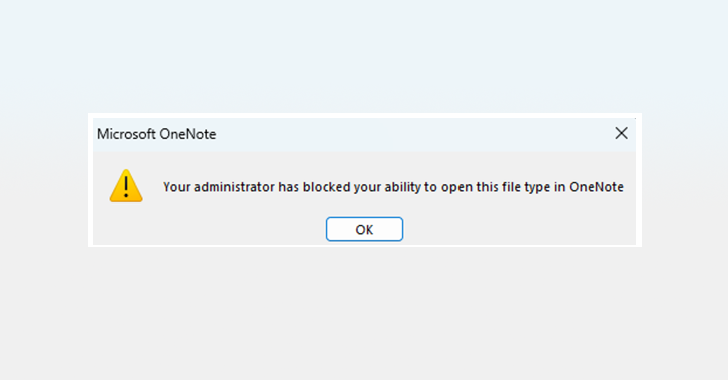
Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions
Microsoft has announced plans to automatically block embedded files with "dangerous extensions" in OneNote following reports that the note-taking service is being increasingly abused for malware delivery. Up until now, users were shown a dialog warning them that opening such attachments could harm their computer and data, but it was possible to dismiss the prompt and open the … [Read more...] about Microsoft Tightens OneNote Security by Auto-Blocking 120 Risky File Extensions
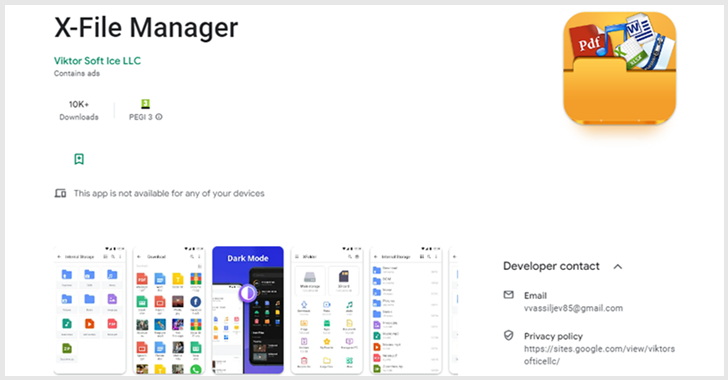
This Android File Manager App Infected Thousands of Devices with SharkBot Malware
The Android banking fraud malware known as SharkBot has reared its head once again on the official Google Play Store, posing as file managers to bypass the app marketplace's restrictions. A majority of the users who downloaded the rogue apps are located in the U.K. and Italy, Romanian cybersecurity company Bitdefender said in an analysis published this week. SharkBot, first … [Read more...] about This Android File Manager App Infected Thousands of Devices with SharkBot Malware
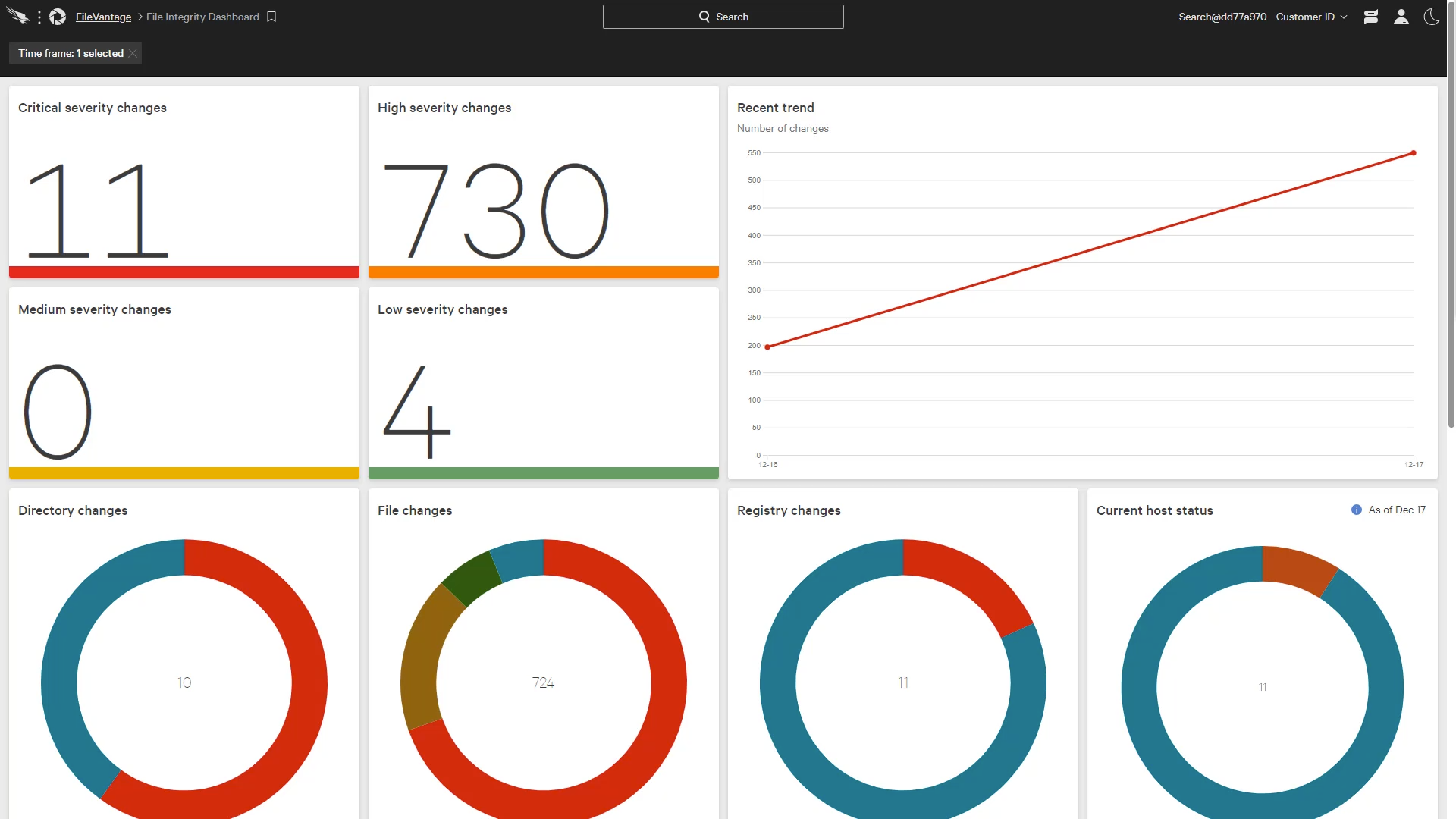
Monitoring File Changes with Falcon FileVantage
Introduction Due to compliance regulations, many organizations have a need to monitor key assets for changes made to certain files, folders or registry settings. File Integrity Monitoring (FIM) can be a daunting deployment that requires yet another solution in the security stack. As a cloud delivered platform, CrowdStrike leverages a single light-weight agent to address a … [Read more...] about Monitoring File Changes with Falcon FileVantage
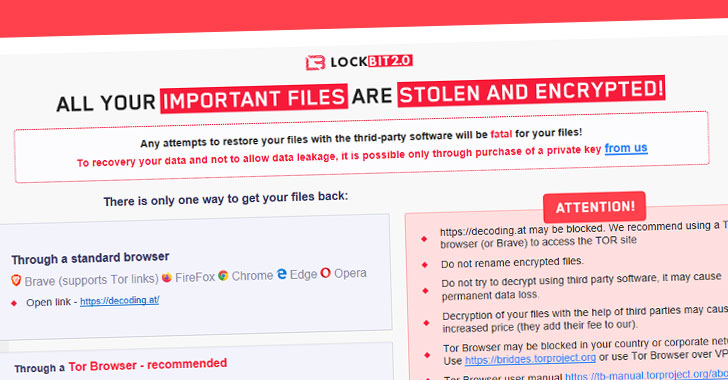
LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
A new ransomware family that emerged last month comes with its own bag of tricks to bypass ransomware protection by leveraging a novel technique called "intermittent encryption." Called LockFile, the operators of the ransomware has been found exploiting recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows servers and deploy file-encrypting malware … [Read more...] about LockFile Ransomware Bypasses Protection Using Intermittent File Encryption
17-Year-Old Weakness in Firefox Let HTML File Steal Other Files From Device
Except for phishing and scams, downloading an HTML attachment and opening it locally on your browser was never considered as a severe threat until a security researcher today demonstrated a technique that could allow attackers to steal files stored on a victim's computer.Barak Tawily, an application security researcher, shared his findings with The Hacker News, wherein he … [Read more...] about 17-Year-Old Weakness in Firefox Let HTML File Steal Other Files From Device
Your Linux Can Get Hacked Just by Opening a File in Vim or Neovim Editor
Linux users, beware!If you haven't recently updated your Linux operating system, especially the command-line text editor utility, do not even try to view the content of a file using Vim or Neovim.Security researcher Armin Razmjou recently discovered a high-severity arbitrary OS command execution vulnerability (CVE-2019-12735) in Vim and Neovim—two most popular and powerful … [Read more...] about Your Linux Can Get Hacked Just by Opening a File in Vim or Neovim Editor