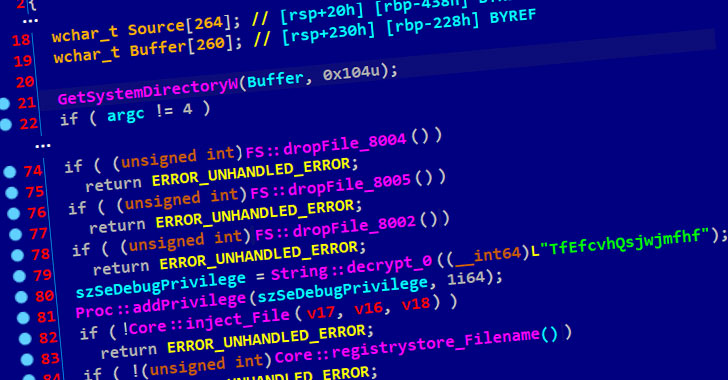
The North Korea-linked ScarCruft group has been attributed to a previously undocumented backdoor called Dolphin that the threat actor has used against targets located in its southern counterpart. "The backdoor [...] has a wide range of spying capabilities, including monitoring drives and portable devices and exfiltrating files of interest, keylogging and taking screenshots, and … [Read more...] about North Korea Hackers Using New “Dolphin” Backdoor to Spy on South Korean Targets
Korea
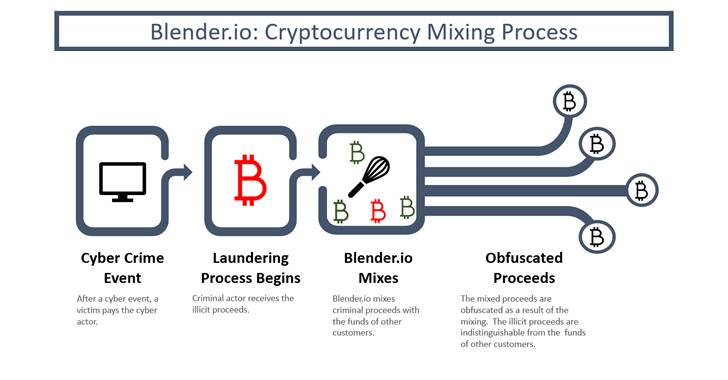
U.S. Sanctions Cryptocurrency Mixer Blender for Helping North Korea Launder Millions
The U.S. Treasury Department on Friday moved to sanction virtual currency mixer Blender.io, marking the first time a mixing service has been subjected to economic blockades. The move signals continued efforts on the part of the government to prevent North Korea's Lazarus Group from laundering the funds stolen from the unprecedented hack of Ronin Bridge in late March. The newly … [Read more...] about U.S. Sanctions Cryptocurrency Mixer Blender for Helping North Korea Launder Millions
North Korea Exploited VPN Flaw to Hack South’s Nuclear Research Institute
South Korea's state-run Korea Atomic Energy Research Institute (KAERI) on Friday disclosed that its internal network was infiltrated by suspected attackers operating out of its northern counterpart. The intrusion is said to have taken place on May 14 through a vulnerability in an unnamed virtual private network (VPN) vendor and involved a total of 13 IP addresses, one of which … [Read more...] about North Korea Exploited VPN Flaw to Hack South’s Nuclear Research Institute
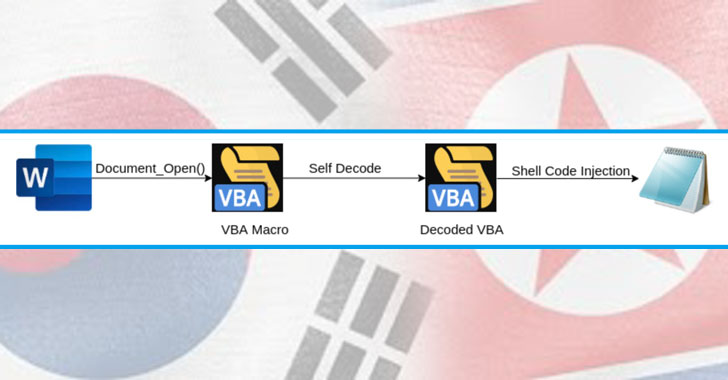
North Korean hackers targeting South Korea with RokRat Trojan
A North Korean hacking group has been found deploying the RokRat Trojan in a new spear-phishing campaign targeting the South Korean government. Attributing the attack to APT37 (aka Starcruft, Ricochet Chollima, or Reaper), Malwarebytes said it identified a malicious document last December that, when opened, executes a macro in memory to install the aforementioned remote access … [Read more...] about North Korean hackers targeting South Korea with RokRat Trojan
Trojanized Security Software Hits South Korea Users in Supply-Chain Attack
Cybersecurity researchers took the wraps off a novel supply chain attack in South Korea that abuses legitimate security software and stolen digital certificates to distribute remote administration tools (RATs) on target systems. Attributing the operation to the Lazarus Group, also known as Hidden Cobra, Slovak internet security company ESET said the state-sponsored threat actor … [Read more...] about Trojanized Security Software Hits South Korea Users in Supply-Chain Attack
EU sanctions hackers from China, Russia, North Korea who’re wanted by the FBI
The Council of the European Union has imposed its first-ever sanctions against persons or entities involved in various cyber-attacks targeting European citizens, and its member states.The directive has been issued against six individuals and three entities responsible for or involved in various cyber-attacks, out of which some publicly known are 'WannaCry', 'NotPetya', and … [Read more...] about EU sanctions hackers from China, Russia, North Korea who’re wanted by the FBI