Below research is reflecting our observations during month of March 2022. We also would like to thank Maria Jose Erquiaga for her contribution in introduction and support during the process of writing. Overview As the Russian-Ukrainian war continues over conventional warfare, cybersecurity professionals witnessed their domain turning into a real frontier. Threat actors picking … [Read more...] about Network Footprints of Gamaredon Group
Network
Critical TLStorm 2.0 Bugs Affect Widely-Used Aruba and Avaya Network Switches
Cybersecurity researchers have detailed as many as five severe security flaws in the implementation of TLS protocol in several models of Aruba and Avaya network switches that could be abused to gain remote access to enterprise networks and steal valuable information. The findings follow the March disclosure of TLStorm, a set of three critical flaws in APC Smart-UPS devices that … [Read more...] about Critical TLStorm 2.0 Bugs Affect Widely-Used Aruba and Avaya Network Switches
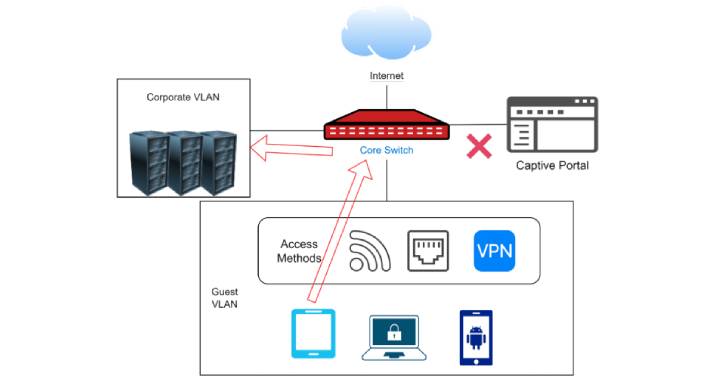
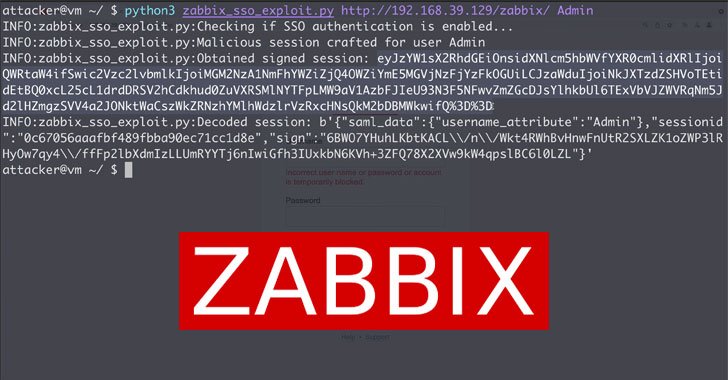
CISA Alerts on Actively Exploited Flaws in Zabbix Network Monitoring Platform
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has warned of active exploitation of two security flaws impacting Zabbix open-source enterprise monitoring platform, adding them to its Known Exploited Vulnerabilities Catalog. On top of that, CISA is also recommending that Federal Civilian Executive Branch (FCEB) agencies patch all systems against the … [Read more...] about CISA Alerts on Actively Exploited Flaws in Zabbix Network Monitoring Platform
Network Security Automation using Cisco Secure Firewall and Hashicorp’s Consul
More and more organizations today are moving towards dynamic infrastructure deployments in cloud environments or using microservices. In such environments, instances and services are created and decommissioned as per need and that can be very frequent. Keeping track of updates to such components in a fast-changing environment is becoming a challenge for SecOps teams and an … [Read more...] about Network Security Automation using Cisco Secure Firewall and Hashicorp’s Consul
Simplify Security at the Virtual Edge with Cisco Secure Firewall and Network Edge from Equinix
Over the last few years, adoption of hybrid and multicloud environments has grown significantly because of the added benefits they provide organizations — including lower initial costs, simplified management, and time savings. As organizations continue to relocate more of their applications to hybrid and multicloud environments, complexity begins to increase, especially when … [Read more...] about Simplify Security at the Virtual Edge with Cisco Secure Firewall and Network Edge from Equinix
Relevant and Extended Detection with SecureX, Part Three: Behaviour-Based Detections with Secure Network Analytics
In part one of this Relevant and Extended Detection with SecureX series, we introduced the notion of risk-based extended detection with Cisco SecureX – the idea that a user can prioritise detections into incidents based on their idea of what constitutes risk in their environments and then extend those detections with enrichments from other products. In subsequent posts we are … [Read more...] about Relevant and Extended Detection with SecureX, Part Three: Behaviour-Based Detections with Secure Network Analytics
New Mobile Network Vulnerabilities Affect All Cellular Generations Since 2G
Researchers have disclosed security vulnerabilities in handover, a fundamental mechanism that undergirds modern cellular networks, which could be exploited by adversaries to launch denial-of-service (DoS) and man-in-the-middle (MitM) attacks using low-cost equipment. The "vulnerabilities in the handover procedure are not limited to one handover case only but they impact all … [Read more...] about New Mobile Network Vulnerabilities Affect All Cellular Generations Since 2G
New EwDoor Botnet Targeting Unpatched AT&T Network Edge Devices
A newly discovered botnet capable of staging distributed denial-of-service (DDoS) attacks targeted unpatched Ribbon Communications (formerly Edgewater Networks) EdgeMarc appliances belonging to telecom service provider AT&T by exploiting a four-year-old flaw in the network appliances. Chinese tech giant Qihoo 360's Netlab network security division, which detected the botnet … [Read more...] about New EwDoor Botnet Targeting Unpatched AT&T Network Edge Devices
Simplify Network Security with Cisco Secure Firewall-as-a-service (FWaaS) on AWS
Introduction With traditional firewalls, network security teams are charged with the heavy lifting of deploying new solutions. They are responsible for a variety of costs, including licensing, appliance, related infrastructure updates, and ongoing maintenance. From a time-value perspective, inserting firewalls also creates additional complexity for NetOps and SecOps teams, … [Read more...] about Simplify Network Security with Cisco Secure Firewall-as-a-service (FWaaS) on AWS
Black Hat Europe 2021 Network Operations Center: London called, We answered
It was so amazing to return to London for the Black Hat Europe 2021 Network Operations Center (NOC). Produced by Informa Tech, and built by the security partners, the mission of the NOC is to quickly build a conference network that is secure, stable and accessible for the briefings, sponsors and attendees. It is a team effort, where collaboration combines a robust backbone … [Read more...] about Black Hat Europe 2021 Network Operations Center: London called, We answered