Oct 16, 2023NewsroomMalware / Mobile Security The Android banking trojan known as SpyNote has been dissected to reveal its diverse information-gathering features. Typically spread via SMS phishing campaigns, attack chains involving the spyware trick potential victims into installing the app by clicking on the embedded link, according to F-Secure. Besides requesting invasive … [Read more...] about Beware of This Android Trojan that Records Audio and Phone Calls
Phone
U.K. Police Arrest 142 in Global Crackdown on ‘iSpoof’ Phone Spoofing Service
A coordinated law enforcement effort has dismantled an online phone number spoofing service called iSpoof and arrested 142 individuals linked to the operation. The websites, ispoof[.]me and ispoof[.]cc, allowed the crooks to "impersonate trusted corporations or contacts to access sensitive information from victims," Europol said in a press statement. Worldwide losses exceeded … [Read more...] about U.K. Police Arrest 142 in Global Crackdown on ‘iSpoof’ Phone Spoofing Service
Hackers Targeting VoIP Servers By Exploiting Digium Phone Software
VoIP phones using Digium's software have been targeted to drop a web shell on their servers as part of an attack campaign designed to exfiltrate data by downloading and executing additional payloads. "The malware installs multilayer obfuscated PHP backdoors to the web server's file system, downloads new payloads for execution, and schedules recurring tasks to re-infect the host … [Read more...] about Hackers Targeting VoIP Servers By Exploiting Digium Phone Software
Spam mail with scammers’ phone numbers
With the colossal amount of telephone scamming these days, you’d be hard-pressed to find a phone owner anywhere on the planet who hasn’t been a scammer’s target at least once. But like all forms of cold calling, phone scams are resource-intensive and highly inefficient. Therefore, some scammers try to optimize the process by getting potential victims to call them. One tool they … [Read more...] about Spam mail with scammers’ phone numbers
New Study Warns of Security Threats Linked to Recycled Phone Numbers
A new academic study has highlighted a number of privacy and security pitfalls associated with recycling mobile phone numbers that could be abused to stage a variety of exploits, including account takeovers, conduct phishing and spam attacks, and even prevent victims from signing up for online services. Nearly 66% of the recycled numbers that were sampled were found to be tied … [Read more...] about New Study Warns of Security Threats Linked to Recycled Phone Numbers
533 Million Facebook Users’ Phone Numbers and Personal Data Leaked Online
In what's likely to be a goldmine for bad actors, personal information associated with approximately 533 million Facebook users worldwide has been leaked on a popular cybercrime forum for free—which was harvested by hackers in 2019 using a Facebook vulnerability. The leaked data includes full names, Facebook IDs, mobile numbers, locations, email addresses, gender, occupation, … [Read more...] about 533 Million Facebook Users’ Phone Numbers and Personal Data Leaked Online
Premium-Rate Phone Fraudsters Hack VoIP Servers of 1200 Companies
Cybersecurity researchers today took the wraps off an on-going cyber fraud operation led by hackers in Gaza, West Bank, and Egypt to compromise VoIP servers of more than 1,200 organizations across 60 countries over the past 12 months. According to findings published by Check Point Research, the threat actors — believed to be located in the Palestinian Gaza Strip — have targeted … [Read more...] about Premium-Rate Phone Fraudsters Hack VoIP Servers of 1200 Companies
Major Instagram App Bug Could’ve Given Hackers Remote Access to Your Phone
Ever wonder how hackers can hack your smartphone remotely? In a report shared with The Hacker News today, Check Point researchers disclosed details about a critical vulnerability in Instagram's Android app that could have allowed remote attackers to take control over a targeted device just by sending victims a specially crafted image. What's more worrisome is that the flaw not … [Read more...] about Major Instagram App Bug Could’ve Given Hackers Remote Access to Your Phone
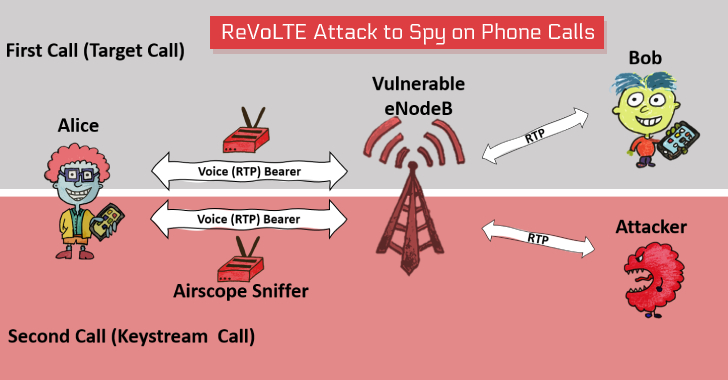
New Attack Lets Hackers Decrypt VoLTE Encryption to Spy on Phone Calls
A team of academic researchers—who previously made the headlines earlier this year for uncovering severe security issues in the 4G LTE and 5G networks—today presented a new attack called 'ReVoLTE,' that could let remote attackers break the encryption used by VoLTE voice calls and spy on targeted phone calls.The attack doesn't exploit any flaw in the Voice over LTE (VoLTE) … [Read more...] about New Attack Lets Hackers Decrypt VoLTE Encryption to Spy on Phone Calls
You Gave Your Phone Number to Twitter for Security and Twitter Used it for Ads
After exposing private tweets, plaintext passwords, and personal information for hundreds of thousands of its users, here is a new security blunder social networking company Twitter admitted today.Twitter announced that the phone numbers and email addresses of some users provided for two-factor authentication (2FA) protection had been used for targeted advertising … [Read more...] about You Gave Your Phone Number to Twitter for Security and Twitter Used it for Ads