Jun 08, 2024NewsroomVulnerability / Programming Details have emerged about a new critical security flaw impacting PHP that could be exploited to achieve remote code execution under certain circumstances. The vulnerability, tracked as CVE-2024-4577, has been described as a CGI argument injection vulnerability affecting all versions of PHP installed on the Windows operating … [Read more...] about New PHP Vulnerability Exposes Windows Servers to Remote Code Execution
remote
Critical Tinyproxy Flaw Opens Over 50,000 Hosts to Remote Code Execution
May 06, 2024NewsroomVulnerability / Server Security More than 50% of the 90,310 hosts have been found exposing a Tinyproxy service on the internet that's vulnerable to a critical unpatched security flaw in the HTTP/HTTPS proxy tool. The issue, tracked as CVE-2023-49606, carries a CVSS score of 9.8 out of a maximum of 10, per Cisco Talos, which described it as a use-after-free … [Read more...] about Critical Tinyproxy Flaw Opens Over 50,000 Hosts to Remote Code Execution
Malicious Code in XZ Utils for Linux Systems Enables Remote Code Execution
Apr 02, 2024NewsroomFirmware Security / Vulnerability The malicious code inserted into the open-source library XZ Utils, a widely used package present in major Linux distributions, is also capable of facilitating remote code execution, a new analysis has revealed. The audacious supply chain compromise, tracked as CVE-2024-3094 (CVSS score: 10.0), came to light last week when … [Read more...] about Malicious Code in XZ Utils for Linux Systems Enables Remote Code Execution
New Juniper Junos OS Flaws Expose Devices to Remote Attacks
Aug 19, 2023THNNetwork Security / Vulnerability Networking hardware company Juniper Networks has released an "out-of-cycle" security update to address multiple flaws in the J-Web component of Junos OS that could be combined to achieve remote code execution on susceptible installations. The four vulnerabilities have a cumulative CVSS rating of 9.8, making them Critical in … [Read more...] about New Juniper Junos OS Flaws Expose Devices to Remote Attacks
Identifying malicious Remote Desktop Protocol (RDP) connections with Elastic Security
Lateral movement is a dangerous threat in the landscape of highly integrated technologies. If attackers gain access to an endpoint, it’s critical for security teams to identify any and all movements they make. To combat this threat, Elastic Security is excited to announce a new lateral movement detection package that makes use of advanced analytics.In the past, we explored how … [Read more...] about Identifying malicious Remote Desktop Protocol (RDP) connections with Elastic Security
New OpenSSH Vulnerability Exposes Linux Systems to Remote Command Injection
Jul 24, 2023THNLinux / Network Security Details have emerged about a now-patched flaw in OpenSSH that could be potentially exploited to run arbitrary commands remotely on compromised hosts under specific conditions. "This vulnerability allows a remote attacker to potentially execute arbitrary commands on vulnerable OpenSSH's forwarded ssh-agent," Saeed Abbasi, manager of … [Read more...] about New OpenSSH Vulnerability Exposes Linux Systems to Remote Command Injection
Rockwell Automation ControlLogix Bugs Expose Industrial Systems to Remote Attacks
Jul 13, 2023THNOT/ICS, SCADA Cybersecurity The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has alerted of two security flaws impacting Rockwell Automation ControlLogix EtherNet/IP (ENIP) communication module models that could be exploited to achieve remote code execution and denial-of-service (DoS). "The results and impact of exploiting these vulnerabilities … [Read more...] about Rockwell Automation ControlLogix Bugs Expose Industrial Systems to Remote Attacks
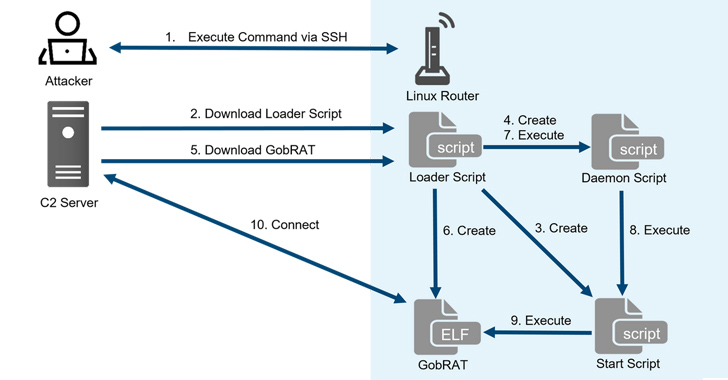
New GobRAT Remote Access Trojan Targeting Linux Routers in Japan
May 29, 2023Ravie LakshmananLinux / Network Security Linux routers in Japan are the target of a new Golang remote access trojan (RAT) called GobRAT. "Initially, the attacker targets a router whose WEBUI is open to the public, executes scripts possibly by using vulnerabilities, and finally infects the GobRAT," the JPCERT Coordination Center (JPCERT/CC) said in a report … [Read more...] about New GobRAT Remote Access Trojan Targeting Linux Routers in Japan
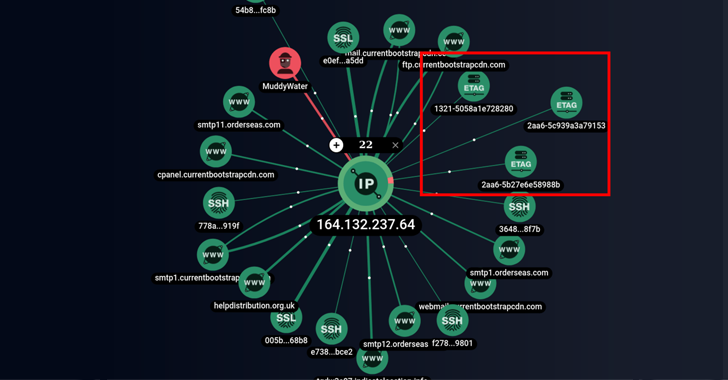
Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access
Apr 18, 2023Ravie LakshmananCyber Threat / Malware The Iranian threat actor known as MuddyWater is continuing its time-tested tradition of relying on legitimate remote administration tools to commandeer targeted systems. While the nation-state group has previously employed ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has revealed the adversary's … [Read more...] about Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access
Zero-click remote hacks for Samsung, Google, and Vivo smartphones
Smartphones, tablets, and even cars with Samsung Exynos microprocessors are at risk of remote hacking. Bug hunters at Google Project Zero say you just need the victim’s phone number. This is due to the presence of 18 vulnerabilities in the Exynos baseband radio processor, which is widely used in Google, Vivo, Samsung, and many other smartphones. Four of them are critical and … [Read more...] about Zero-click remote hacks for Samsung, Google, and Vivo smartphones