CrowdStrike is proud to announce the launch of CrowdStrike Counter Adversary Operations, a newly formed, first-of-its kind team that brings together CrowdStrike Falcon® Intelligence and the CrowdStrike® Falcon OverWatch™ threat hunting team to disrupt today’s adversaries and ultimately raise their cost of doing business. Both threat hunting and intelligence operations are … [Read more...] about CrowdStrike Debuts Counter Adversary Ops Team
Team
Making PAM Great Again: Solving the Top 5 Identity Team PAM Challenges
Aug 04, 2023The Hacker News Privileged Access Management (PAM) solutions are widely acknowledged as the gold standard for securing critical privileged accounts. However, many security and identity teams face inherent obstacles during the PAM journey, hindering these solutions from reaching their full potential. These challenges deprive organizations of the resilience they … [Read more...] about Making PAM Great Again: Solving the Top 5 Identity Team PAM Challenges
Chinese Tonto Team Hackers’ Second Attempt to Target Cybersecurity Firm Group-IB Fails
Feb 13, 2023Ravie LakshmananCyber Threat Intelligence The advanced persistent threat (APT) actor known as Tonto Team carried out an unsuccessful attack on cybersecurity company Group-IB in June 2022. The Singapore-headquartered firm said that it detected and blocked malicious phishing emails originating from the group targeting its employees. It's also the second attack aimed … [Read more...] about Chinese Tonto Team Hackers’ Second Attempt to Target Cybersecurity Firm Group-IB Fails
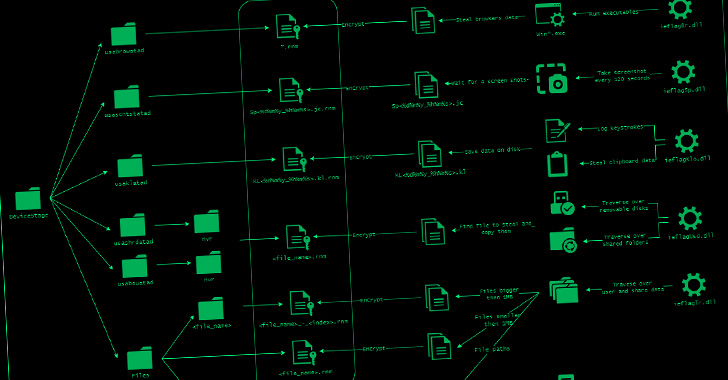
DoNot Team Hackers Updated its Malware Toolkit with Improved Capabilities
The Donot Team threat actor has updated its Jaca Windows malware toolkit with improved capabilities, including a revamped stealer module designed to plunder information from Google Chrome and Mozilla Firefox browsers. The improvements also include a new infection chain that incorporates previously undocumented components to the modular framework, Morphisec researchers Hido … [Read more...] about DoNot Team Hackers Updated its Malware Toolkit with Improved Capabilities
A Key Factor for Platform Team To Be Successful
Centralize or decentralize, what cycle are we in?As an industry analyst at Gartner, we would often discuss whether people were in a centralized or decentralized cycle. In business, it’s normal to investigate options for creating innovation and moving quickly, or focus on reducing cost and optimizing teams and technologies. The current cycle we have been in has lasted roughly10 … [Read more...] about A Key Factor for Platform Team To Be Successful
Justice Department Appoints First Director of National Cryptocurrency Enforcement Team
The U.S. Department of Justice (DoJ) earlier this week appointed Eun Young Choi to serve as the first Director of the National Cryptocurrency Enforcement Team (NCET) it established last year. The NCET was created to tackle the criminal misuse of cryptocurrencies and digital assets," with a focus on illegal activities in virtual currency exchanges, mixing and tumbling services, … [Read more...] about Justice Department Appoints First Director of National Cryptocurrency Enforcement Team
Meet CrowdStrike’s Strategic Counter-Adversarial Research Team (SCAR)
As a human-led managed threat hunting service, CrowdStrike Falcon OverWatch™ is built around the best and brightest analysts in the industry who lead the fight against today’s sophisticated adversaries. But while humans remain the critical ingredient that makes OverWatch so successful, these hunters are also supported by best-in-class technologies that enable them to work at … [Read more...] about Meet CrowdStrike’s Strategic Counter-Adversarial Research Team (SCAR)
4 Keys to Create a Thriving Cybersecurity Team for Long-Term Success
There has never been a more important time to listen. “Seek first to understand,” is a lesson I picked up early in my career that has generally proved effective in many situations as a leader, colleague and employee. (Not to mention at home as a partner, father, and friend; it’s a versatile maxim.) Eighteen months into this pandemic, given that the experience and effects of … [Read more...] about 4 Keys to Create a Thriving Cybersecurity Team for Long-Term Success
Meet the Cisco Telemetry Broker Team: Ajit Thyagarajan
Introduction In my previous blog in this series, I spoke with Sunil Amin about his work on the Cisco Telemetry Broker, the hot new product that allows customers to finally have the telemetry across their business be programmable and available to any analytics platform. Today I’m here with Ajit Thyagarajan who is responsible for the architecture of the Cisco Telemetry Broker. … [Read more...] about Meet the Cisco Telemetry Broker Team: Ajit Thyagarajan
Meet the Cisco Telemetry Broker Team: Sunil Amin
Introduction The Cisco Telemetry Broker celebrated its release earlier this month on April 1st. In my previous blog, The Rise of Telemetry Architecture, I discussed how the Cisco Telemetry Broker can help you develop a healthy telemetry architecture. This time around, I’ll be taking a look at what went into creating the product, how its roots in the Stealthwatch UDP Director … [Read more...] about Meet the Cisco Telemetry Broker Team: Sunil Amin