Users in Brazil are the target of a new banking trojan known as CHAVECLOAK that's propagated via phishing emails bearing PDF attachments. "This intricate attack involves the PDF downloading a ZIP file and subsequently utilizing DLL side-loading techniques to execute the final malware," Fortinet FortiGuard Labs researcher Cara Lin said. The attack chain involves the use of … [Read more...] about New Banking Trojan CHAVECLOAK Targets Brazilian Users via Phishing Tactics
Tactics
Carbanak Banking Malware Resurfaces with New Ransomware Tactics
Dec 26, 2023NewsroomMalware / Cybercrime The banking malware known as Carbanak has been observed being used in ransomware attacks with updated tactics. "The malware has adapted to incorporate attack vendors and techniques to diversify its effectiveness," cybersecurity firm NCC Group said in an analysis of ransomware attacks that took place in November 2023. "Carbanak returned … [Read more...] about Carbanak Banking Malware Resurfaces with New Ransomware Tactics
New Advanced Backdoor with Distinctive Malware Tactics
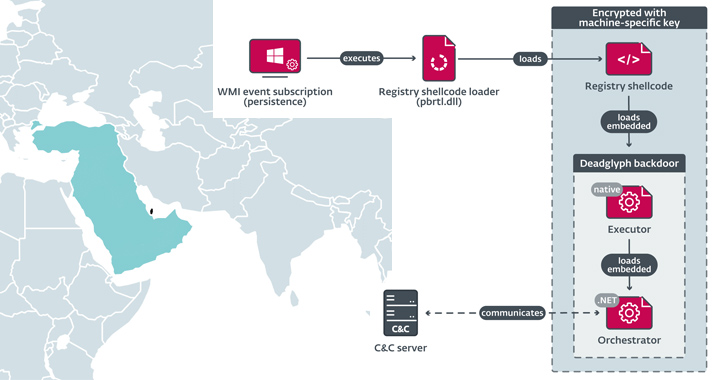
Sep 23, 2023THNCyber Espionage / Malware Cybersecurity researchers have discovered a previously undocumented advanced backdoor dubbed Deadglyph employed by a threat actor known as Stealth Falcon as part of a cyber espionage campaign. "Deadglyph's architecture is unusual as it consists of cooperating components – one a native x64 binary, the other a .NET assembly," ESET said … [Read more...] about New Advanced Backdoor with Distinctive Malware Tactics
Diicot Expands Tactics with Cayosin Botnet
Jun 17, 2023Ravie LakshmananCryptojacking / Network Security Cybersecurity researchers have discovered previously undocumented payloads associated with a Romanian threat actor named Diicot, revealing its potential for launching distributed denial-of-service (DDoS) attacks. "The Diicot name is significant, as it's also the name of the Romanian organized crime and … [Read more...] about Diicot Expands Tactics with Cayosin Botnet
Improved BlackCat Ransomware Strikes with Lightning Speed and Stealthy Tactics
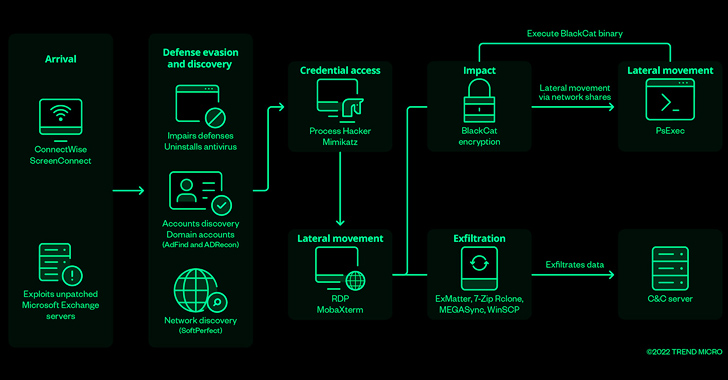
Jun 01, 2023Ravie LakshmananEndpoint Security / Encryption The threat actors behind BlackCat ransomware have come up with an improved variant that prioritizes speed and stealth in an attempt to bypass security guardrails and achieve their goals. The new version, dubbed Sphynx and announced in February 2023, packs a "number of updated capabilities that strengthen the group's … [Read more...] about Improved BlackCat Ransomware Strikes with Lightning Speed and Stealthy Tactics
Vietnamese Threat Actor Infects 500,000 Devices Using ‘Malverposting’ Tactics
May 01, 2023Ravie LakshmananMalverposting / Scam A Vietnamese threat actor has been attributed as behind a "malverposting" campaign on social media platforms to infect over 500,000 devices worldwide over the past three months to deliver variants of information stealers such as S1deload Stealer and SYS01stealer. Malverposting refers to the use of promoted social media posts on … [Read more...] about Vietnamese Threat Actor Infects 500,000 Devices Using ‘Malverposting’ Tactics
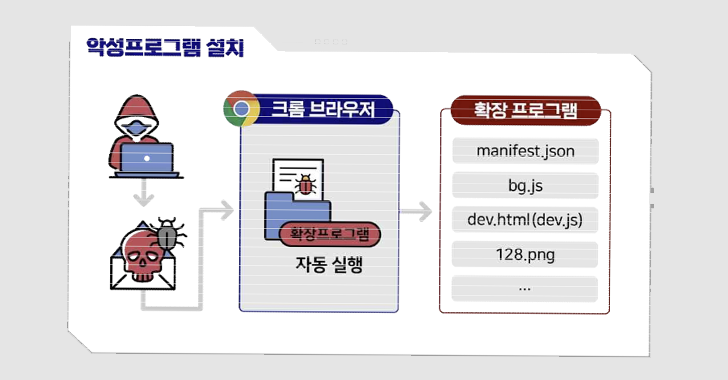
German and South Korean Agencies Warn of Kimsuky’s Expanding Cyber Attack Tactics
Mar 23, 2023Ravie LakshmananCyber Attack / Browser Security German and South Korean government agencies have warned about cyber attacks mounted by a threat actor tracked as Kimsuky using rogue browser extensions to steal users' Gmail inboxes. The joint advisory comes from Germany's domestic intelligence apparatus, the Federal Office for the Protection of the Constitution … [Read more...] about German and South Korean Agencies Warn of Kimsuky’s Expanding Cyber Attack Tactics
SysUpdate Malware Strikes Again with Linux Version and New Evasion Tactics
Mar 02, 2023Ravie LakshmananLinux / Cyber Threat The threat actor known as Lucky Mouse has developed a Linux version of a malware toolkit called SysUpdate, expanding on its ability to target devices running the operating system. The oldest version of the updated artifact dates back to July 2022, with the malware incorporating new features designed to evade security software … [Read more...] about SysUpdate Malware Strikes Again with Linux Version and New Evasion Tactics
Hackers Using CAPTCHA Bypass Tactics in Freejacking Campaign on GitHub
Jan 06, 2023Ravie LakshmananCryptocurrency / GitHub A South Africa-based threat actor known as Automated Libra has been observed employing CAPTCHA bypass techniques to create GitHub accounts in a programmatic fashion as part of a freejacking campaign dubbed PURPLEURCHIN. The group "primarily targets cloud platforms offering limited-time trials of cloud resources in order to … [Read more...] about Hackers Using CAPTCHA Bypass Tactics in Freejacking Campaign on GitHub
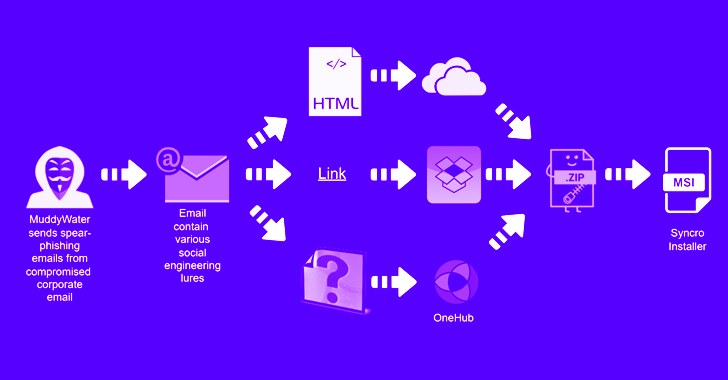
MuddyWater Hackers Target Asian and Middle East Countries with Updated Tactics
Dec 09, 2022Ravie LakshmananThreat Intelligence / Cyber Attack The Iran-linked MuddyWater threat actor has been observed targeting several countries in the Middle East as well as Central and West Asia as part of a new spear-phishing activity. "The campaign has been observed targeting Armenia, Azerbaijan, Egypt, Iraq, Israel, Jordan, Oman, Qatar, Tajikistan, and the United … [Read more...] about MuddyWater Hackers Target Asian and Middle East Countries with Updated Tactics