Elastic Cloud gives you the flexibility to run where and how you want. Deploy in the cloud on Google Cloud, Microsoft Azure, Amazon Web Services, or all the above. You can choose to use our managed service offering or manage the service yourself with built-in automation and orchestration tools.When you log in to the Elastic Cloud console, simply select your region and preferred … [Read more...] about Elastic Cloud is now available on Amazon Web Services (Zurich)
Web
A New Way To Manage Your Web Exposure: The Reflectiz Product Explained
An in-depth look into a proactive website security solution that continuously detects, prioritizes, and validates web threats, helping to mitigate security, privacy, and compliance risks. Reflectiz shields websites from client-side attacks, supply chain risks, data breaches, privacy violations, and compliance issues. You Can't Protect What You Can't See Today's websites are … [Read more...] about A New Way To Manage Your Web Exposure: The Reflectiz Product Explained
New ‘HrServ.dll’ Web Shell Detected in APT Attack Targeting Afghan Government
Nov 25, 2023NewsroomCyber Attack / Threat Intelligence An unspecified government entity in Afghanistan was targeted by a previously undocumented web shell called HrServ in what's suspected to be an advanced persistent threat (APT) attack. The web shell, a dynamic-link library (DLL) named "hrserv.dll," exhibits "sophisticated features such as custom encoding methods for client … [Read more...] about New ‘HrServ.dll’ Web Shell Detected in APT Attack Targeting Afghan Government
What are web skimmers? | Kaspersky official blog
There are a few fairly simple rules that can help you protect both yourself and your money from typical scams while online shopping. Here’s what these boil down to: Don’t send money to personal accounts of strangers on the internet; Don’t enter your bank card details on suspicious sites; Always check the web address carefully before leaving your payment details on a … [Read more...] about What are web skimmers? | Kaspersky official blog
Falcon Intelligence Recon+ and the Dark Web
The vastness of the deep and dark web can easily turn attempts to monitor for cyber threats into a firehose of useless information. Part of the problem is the nature of the data streams that need to be monitored. Every day, more credentials are stolen and exposed. Illegal criminal forums are full of repeated spamming of illicit advertisements. Thousands of new domain names are … [Read more...] about Falcon Intelligence Recon+ and the Dark Web
Magento, WooCommerce, WordPress, and Shopify Exploited in Web Skimmer Attack
Jun 05, 2023Ravie LakshmananWebsite Security / Magecart Cybersecurity researchers have unearthed a new ongoing Magecart-style web skimmer campaign that's designed to steal personally identifiable information (PII) and credit card data from e-commerce websites. A noteworthy aspect that sets it apart from other Magecart campaigns is that the hijacked sites further serve as … [Read more...] about Magento, WooCommerce, WordPress, and Shopify Exploited in Web Skimmer Attack
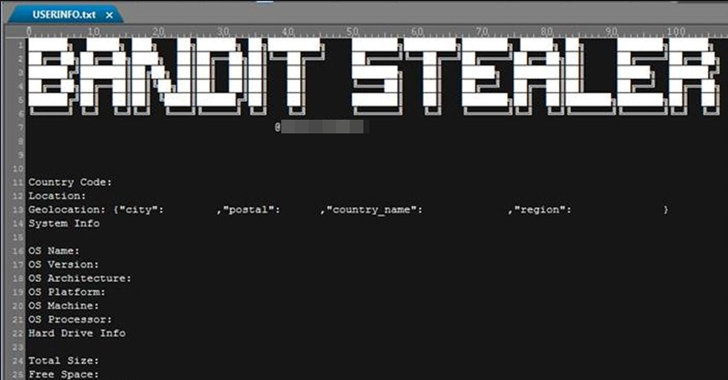
New Stealthy Bandit Stealer Targeting Web Browsers and Cryptocurrency Wallets
A new stealthy information stealer malware called Bandit Stealer has caught the attention of cybersecurity researchers for its ability to target numerous web browsers and cryptocurrency wallets. "It has the potential to expand to other platforms as Bandit Stealer was developed using the Go programming language, possibly allowing cross-platform compatibility," Trend Micro said … [Read more...] about New Stealthy Bandit Stealer Targeting Web Browsers and Cryptocurrency Wallets
New All-in-One “EvilExtractor” Stealer for Windows Systems Surfaces on the Dark Web
Apr 24, 2023Ravie LakshmananCyber Risk / Dark Web A new "all-in-one" stealer malware named EvilExtractor (also spelled Evil Extractor) is being marketed for sale for other threat actors to steal data and files from Windows systems. "It includes several modules that all work via an FTP service," Fortinet FortiGuard Labs researcher Cara Lin said. "It also contains environment … [Read more...] about New All-in-One “EvilExtractor” Stealer for Windows Systems Surfaces on the Dark Web
CISA Issues Warning on Active Exploitation of ZK Java Web Framework Vulnerability
Feb 28, 2023Ravie LakshmananSoftware Security / Cyber Attack The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity flaw affecting the ZK Framework to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation. Tracked as CVE-2022-36537 (CVSS score: 7.5), the issue impacts ZK Framework versions 9.6.1, … [Read more...] about CISA Issues Warning on Active Exploitation of ZK Java Web Framework Vulnerability
Researchers Detail New Attack Method to Bypass Popular Web Application Firewalls
Dec 10, 2022Ravie LakshmananWeb App Firewall / Web Security A new attack method can be used to circumvent web application firewalls (WAFs) of various vendors and infiltrate systems, potentially enabling attackers to gain access to sensitive business and customer information. Web application firewalls are a key line of defense to help filter, monitor, and block HTTP(S) traffic … [Read more...] about Researchers Detail New Attack Method to Bypass Popular Web Application Firewalls