Mar 15, 2024NewsroomData Privacy / Artificial Intelligence Cybersecurity researchers have found that third-party plugins available for OpenAI ChatGPT could act as a new attack surface for threat actors looking to gain unauthorized access to sensitive data. According to new research published by Salt Labs, security flaws found directly in ChatGPT and within the ecosystem could … [Read more...] about Third-Party ChatGPT Plugins Could Lead to Account Takeovers
Account
Mastodon Vulnerability Allows Hackers to Hijack Any Decentralized Account
Feb 03, 2024NewsroomVulnerability / Social Media The decentralized social network Mastodon has disclosed a critical security flaw that enables malicious actors to impersonate and take over any account. "Due to insufficient origin validation in all Mastodon, attackers can impersonate and take over any remote account," the maintainers said in a terse advisory. The … [Read more...] about Mastodon Vulnerability Allows Hackers to Hijack Any Decentralized Account
Google Kubernetes Misconfig Lets Any Gmail Account Control Your Clusters
Jan 24, 2024NewsroomCloud Security / Kubernetes Cybersecurity researchers have discovered a loophole impacting Google Kubernetes Engine (GKE) that could be potentially exploited by threat actors with a Google account to take control of a Kubernetes cluster. The critical shortcoming has been codenamed Sys:All by cloud security firm Orca. As many as 250,000 active GKE clusters … [Read more...] about Google Kubernetes Misconfig Lets Any Gmail Account Control Your Clusters
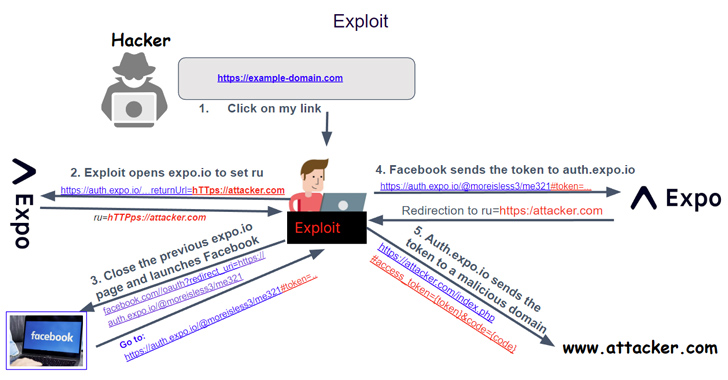
Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking
May 27, 2023Ravie LakshmananAPI Security / Vulnerability A critical security vulnerability has been disclosed in the Open Authorization (OAuth) implementation of the application development framework Expo.io. The shortcoming, assigned the CVE identifier CVE-2023-28131, has a severity rating of 9.6 on the CVSS scoring system. API security firm Salt Labs said the issue rendered … [Read more...] about Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking
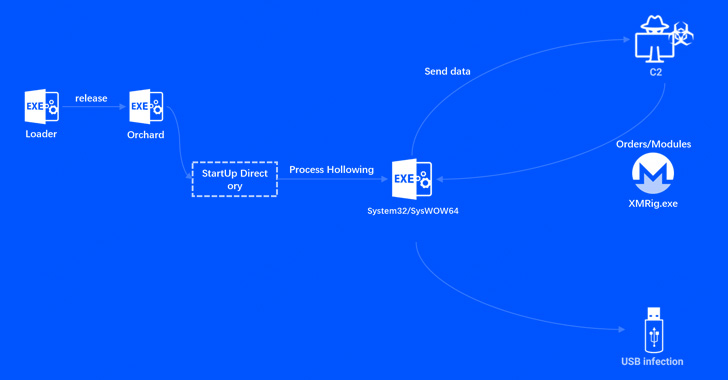
New Orchard Botnet Uses Bitcoin Founder’s Account Info to Generate Malicious Domains
A new botnet named Orchard has been observed using Bitcoin creator Satoshi Nakamoto's account transaction information to generate domain names to conceal its command-and-control (C2) infrastructure. "Because of the uncertainty of Bitcoin transactions, this technique is more unpredictable than using the common time-generated [domain generation algorithms], and thus more … [Read more...] about New Orchard Botnet Uses Bitcoin Founder’s Account Info to Generate Malicious Domains
GitLab Issues Security Patch for Critical Account Takeover Vulnerability
GitLab has moved to address a critical security flaw in its service that, if successfully exploited, could result in an account takeover. Tracked as CVE-2022-1680, the issue has a CVSS severity score of 9.9 and was discovered internally by the company. The security flaw affects all versions of GitLab Enterprise Edition (EE) starting from 11.10 before 14.9.5, all versions … [Read more...] about GitLab Issues Security Patch for Critical Account Takeover Vulnerability
One-Click Exploit Could Have Let Attackers Hijack Any Atlassian Account
Cybersecurity researchers on Wednesday disclosed critical flaws in the Atlassian project and software development platform that could be exploited to take over an account and control some of the apps connected through its single sign-on (SSO) capability. "With just one click, an attacker could have used the flaws to get access to Atlassian's publish Jira system and get … [Read more...] about One-Click Exploit Could Have Let Attackers Hijack Any Atlassian Account
WhatsApp Will Delete Your Account If You Don’t Agree Sharing Data With Facebook
"Respect for your privacy is coded into our DNA," opens WhatsApp's privacy policy. "Since we started WhatsApp, we've aspired to build our Services with a set of strong privacy principles in mind." But come February 8, 2021, this opening statement will no longer find a place in the policy. The Facebook-owned messaging service is alerting users in India of an update to its terms … [Read more...] about WhatsApp Will Delete Your Account If You Don’t Agree Sharing Data With Facebook
Secret Backdoor Account Found in Several Zyxel Firewall, VPN Products
Zyxel has released a patch to address a critical vulnerability in its firmware concerning a hardcoded undocumented secret account that could be abused by an attacker to login with administrative privileges and compromise its networking devices. The flaw, tracked as CVE-2020-29583 (CVSS score 7.8), affects version 4.60 present in wide-range of Zyxel devices, including Unified … [Read more...] about Secret Backdoor Account Found in Several Zyxel Firewall, VPN Products
Any Chingari App (Indian TikTok Clone) Account Can Be Hacked Easily
Following vulnerability disclosure in the Mitron app, another viral TikTok clone in India has now been found vulnerable to a critical but easy-to-exploit authentication bypass vulnerability, allowing anyone to hijack any user account and tamper with their information, content, and even upload unauthorized videos.The Indian video sharing app, called Chingari, is available for … [Read more...] about Any Chingari App (Indian TikTok Clone) Account Can Be Hacked Easily