Elastic Cloud gives you the flexibility to run where and how you want. Deploy in the cloud on Google Cloud, Microsoft Azure, Amazon Web Services, or all the above. You can choose to use our managed service offering or manage the service yourself with built-in automation and orchestration tools.When you log in to the Elastic Cloud console, simply select your region and preferred … [Read more...] about Elastic Cloud is now available on Amazon Web Services (Zurich)
amazon
How Elastic AI Assistant for Security and Amazon Bedrock can empower security analysts for enhanced performance
Elastic Cloud enables users to search, solve, and succeed with one platform, three search-powered solutions, built on a single technology stack. It is designed for any type of data — deployable anywhere — to solve your search, observability, and security challenges. Elastic® users benefit from a unified data analytics platform, which dramatically reduces the cost and complexity … [Read more...] about How Elastic AI Assistant for Security and Amazon Bedrock can empower security analysts for enhanced performance
Revolutionizing big data management: Unveiling the power of Amazon EMR and Elastic integration
In the dynamic realm of data processing, Amazon EMR takes center stage as an AWS-provided big data service, offering a cost-effective conduit for running Apache Spark and a plethora of other open-source applications. While the capabilities of EMR are impressive, the art of vigilant monitoring holds the key to unlocking its full potential. This blog post explains the pivotal … [Read more...] about Revolutionizing big data management: Unveiling the power of Amazon EMR and Elastic integration
Build a GenAI solution using Elastic and Amazon SageMaker JumpStart
In the rapidly advancing world of artificial intelligence, one of the most intriguing and transformative developments is generative artificial intelligence (GAI). GAI represents a significant leap forward in AI capabilities, enabling machines to generate original and creative content across various domains including conversations, stories, images, videos, and music. Enterprises … [Read more...] about Build a GenAI solution using Elastic and Amazon SageMaker JumpStart
Using the Elastic Agent to monitor Amazon ECS and AWS Fargate with Elastic Observability
Serverless and AWS ECS FargateAWS Fargate is a serverless pay-as-you-go engine used for Amazon Elastic Container Service (ECS) to run Docker containers without having to manage servers or clusters. The goal of Fargate is to containerize your application and specify the OS, CPU and memory, networking, and IAM policies needed for launch. Additionally, AWS Fargate can be used with … [Read more...] about Using the Elastic Agent to monitor Amazon ECS and AWS Fargate with Elastic Observability
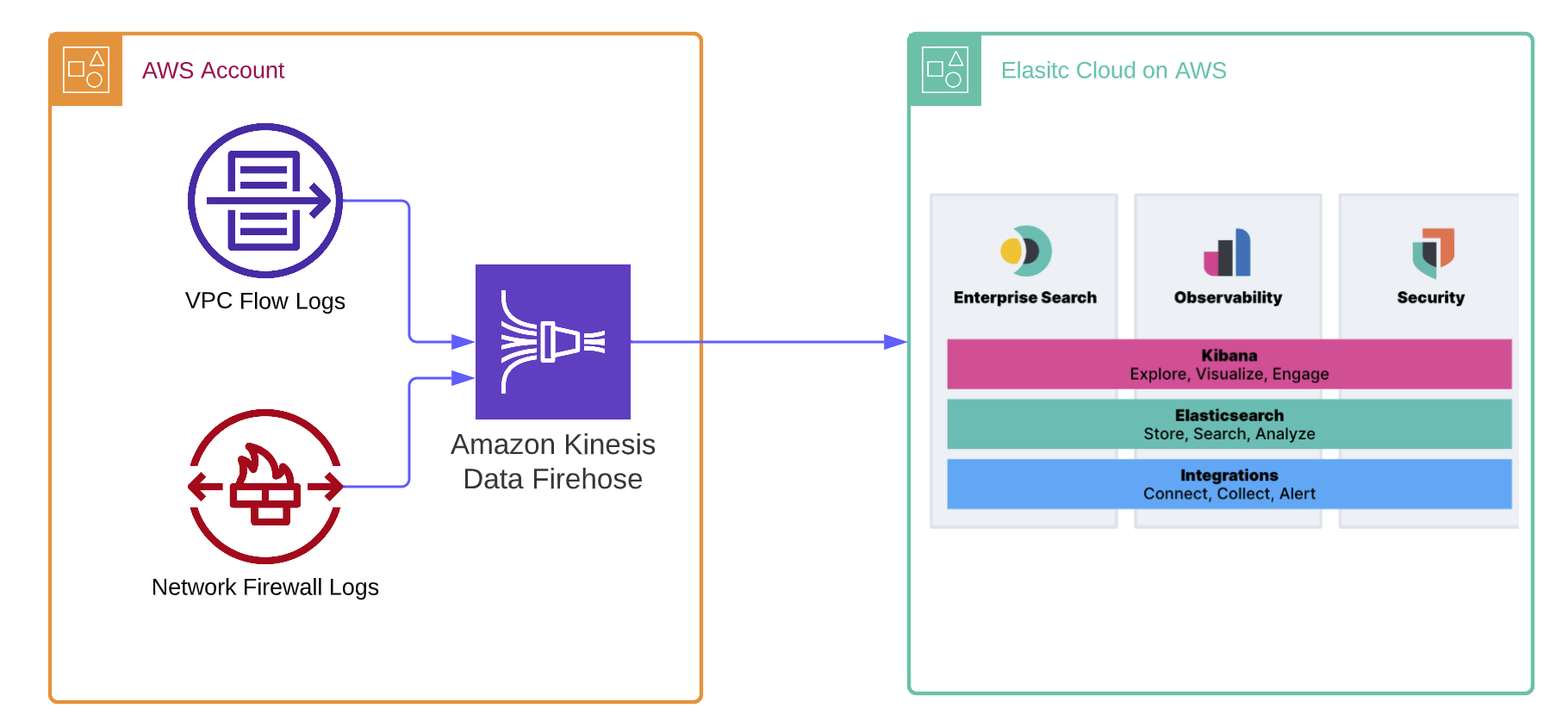
Unleash the power of Amazon Kinesis Data Firehose and Elastic for enhanced observability
As more organizations leverage the Amazon Web Services (AWS) cloud platform and services to drive operational efficiency and bring products to market, managing logs becomes a critical component of maintaining visibility and safeguarding multi-account AWS environments. Traditionally, logs are stored in Amazon Simple Storage Service (Amazon S3) and then shipped to an external … [Read more...] about Unleash the power of Amazon Kinesis Data Firehose and Elastic for enhanced observability
Cisco Joins the Launch of Amazon Security Lake
Cisco supports the Open Cybersecurity Schema Framework and is a launch partner of AWS Security Lake The Cisco Secure Technical Alliance supports the open ecosystem and AWS is a valued technology alliance partner, with integrations across the Cisco Secure portfolio, including SecureX, Secure Firewall, Secure Cloud Analytics, Duo, Umbrella, Web Security Appliance, Secure … [Read more...] about Cisco Joins the Launch of Amazon Security Lake
New Amazon Kindle Bug Could’ve Let Attackers Hijack Your eBook Reader
Amazon earlier this April addressed a critical vulnerability in its Kindle e-book reader platform that could have been potentially exploited to take full control over a user's device, resulting in the theft of sensitive information by just deploying a malicious e-book. "By sending Kindle users a single malicious e-book, a threat actor could have stolen any information stored on … [Read more...] about New Amazon Kindle Bug Could’ve Let Attackers Hijack Your eBook Reader
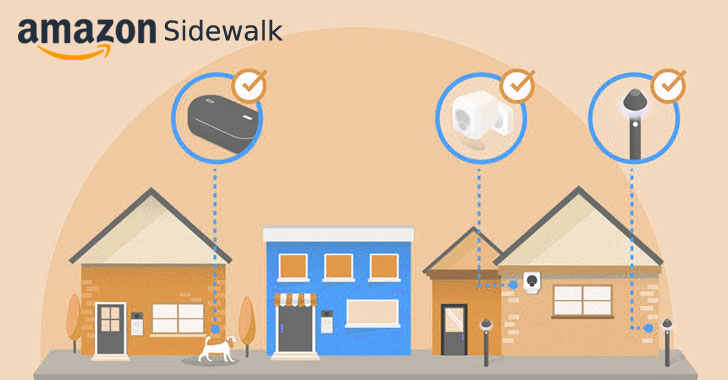
Your Amazon Devices to Automatically Share Your Wi-Fi With Neighbors
Starting June 8, Amazon will automatically enable a feature on your Alexa, Echo, or other Amazon device that will share some of your Internet bandwidth with your neighbors—unless you choose to opt out. Amazon intends to register its family of hardware devices that are operational in the U.S.—including Echo speakers, Ring Video Doorbells, Ring Floodlight … [Read more...] about Your Amazon Devices to Automatically Share Your Wi-Fi With Neighbors
Malicious Amazon Alexa Skills Can Easily Bypass Vetting Process
Researchers have uncovered gaps in Amazon's skill vetting process for the Alexa voice assistant ecosystem that could allow a malicious actor to publish a deceptive skill under any arbitrary developer name and even make backend code changes after approval to trick users into giving up sensitive information. The findings were presented on Wednesday at the Network and Distributed … [Read more...] about Malicious Amazon Alexa Skills Can Easily Bypass Vetting Process