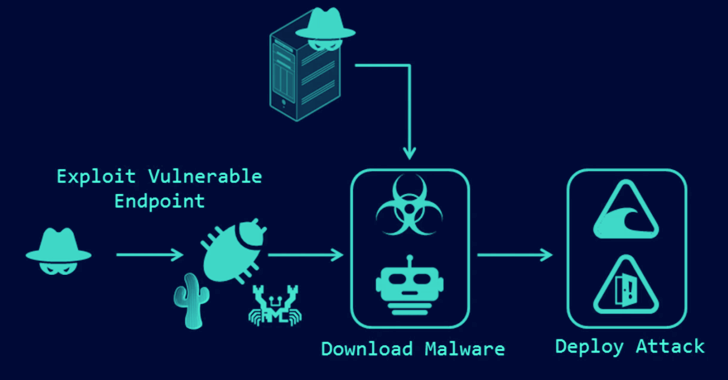
Several serious vulnerabilities have been discovered in Telit Cinterion cellular M2M modems, including the possibility of remote arbitrary code execution (RCE) via SMS messages. These modems are used in millions of different devices and systems for both the consumer market segment (payment terminals, ATMs, cars) and various industries such as healthcare, financial, … [Read more...] about Critical vulnerabilities in Telit Cinterion modems
Vulnerabilities
Google Using Clang Sanitizers to Protect Android Against Cellular Baseband Vulnerabilities
Dec 13, 2023NewsroomMobile Communication / Firmware security Google is highlighting the role played by Clang sanitizers in hardening the security of the cellular baseband in the Android operating system and preventing specific kinds of vulnerabilities. This comprises Integer Overflow Sanitizer (IntSan) and BoundsSanitizer (BoundSan), both of which are part of … [Read more...] about Google Using Clang Sanitizers to Protect Android Against Cellular Baseband Vulnerabilities
3 Critical Vulnerabilities Expose ownCloud Users to Data Breaches
Nov 25, 2023NewsroomData Security / Vulnerability The maintainers of the open-source file-sharing software ownCloud have warned of three critical security flaws that could be exploited to disclose sensitive information and modify files. A brief description of the vulnerabilities is as follows - Disclosure of sensitive credentials and configuration in containerized … [Read more...] about 3 Critical Vulnerabilities Expose ownCloud Users to Data Breaches
U.S. Cybersecurity Agency Adds 6 Flaws to Known Exploited Vulnerabilities Catalog
Jun 24, 2023Ravie LakshmananThreat Intel / Zero Day The U.S. Cybersecurity and Infrastructure Security Agency has added a batch of six flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. This comprises three vulnerabilities that Apple patched this week (CVE-2023-32434, CVE-2023-32435, and CVE-2023-32439), two flaws in VMware … [Read more...] about U.S. Cybersecurity Agency Adds 6 Flaws to Known Exploited Vulnerabilities Catalog
Case study: smart pet feeder vulnerabilities
All animal owners love their pets. And what do pets love above all else? TLC and food, of course. Or vice versa: food first, tummy-rub second. Today’s smart feeders are designed to make sure your pet won’t go hungry or get bored while you’re away. But what’s the score cybersecurity-wise? Not great… Smart feeder for furry friends Smart feeders are becoming a popular choice for … [Read more...] about Case study: smart pet feeder vulnerabilities
New Critical MOVEit Transfer SQL Injection Vulnerabilities Discovered
Jun 10, 2023Ravie LakshmananVulnerability / Cyber Threat Progress Software, the company behind the MOVEit Transfer application, has released patches to address brand new SQL injection vulnerabilities affecting the file transfer solution that could enable the theft of sensitive information. "Multiple SQL injection vulnerabilities have been identified in the MOVEit Transfer web … [Read more...] about New Critical MOVEit Transfer SQL Injection Vulnerabilities Discovered
Cisco and VMware Address Critical Vulnerabilities
Jun 08, 2023Ravie LakshmananNetwork Security / Vulnerability VMware has released security updates to fix a trio of flaws in Aria Operations for Networks that could result in information disclosure and remote code execution. The most critical of the three vulnerabilities is a command injection vulnerability tracked as CVE-2023-20887 (CVSS score: 9.8) that could allow a … [Read more...] about Cisco and VMware Address Critical Vulnerabilities
Severe Android and Novi Survey Vulnerabilities Under Active Exploitation
Apr 14, 2023Ravie LakshmananMobile Security / Cyber Threat The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The two flaws are listed below - CVE-2023-20963 (CVSS score: 7.8) - Android Framework Privilege Escalation … [Read more...] about Severe Android and Novi Survey Vulnerabilities Under Active Exploitation
Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation
Apr 01, 2023Ravie LakshmananCyber Attack / Vulnerability Critical security flaws in Cacti, Realtek, and IBM Aspera Faspex are being exploited by various threat actors in hacks targeting unpatched systems. This entails the abuse of CVE-2022-46169 (CVSS score: 9.8) and CVE-2021-35394 (CVSS score: 9.8) to deliver MooBot and ShellBot (aka PerlBot), Fortinet FortiGuard Labs said … [Read more...] about Cacti, Realtek, and IBM Aspera Faspex Vulnerabilities Under Active Exploitation
55 Zero-Day Vulnerabilities Weaponized in 2022
Mar 21, 2023Ravie LakshmananCyber Threat Intel / Vulnerability As many as 55 zero-day vulnerabilities were exploited in the wild in 2022, with most of the flaws discovered in software from Microsoft, Google, and Apple. While this figure represents a decrease from the year before, when a staggering 81 zero-days were weaponized, it still represents a significant uptick in … [Read more...] about 55 Zero-Day Vulnerabilities Weaponized in 2022